VDI is a virtualization technology where desktop environments are hosted on centralized servers and delivered to endpoint devices over a network. In cyber security, this approach minimizes risk by ensuring that sensitive data and applications remain on secure servers, not on user devices. It provides controlled access, mitigates exposure to malware, and reduces the attack […]
What is VDI in Cyber Security?
The Best Free Open-Source Hypervisors
Searching for the best free open-source hypervisors? Below, we’ll break down some of the best Type 1 (bare metal) and Type 2 (hosted) freeware hypervisors, including some specialized hypervisors for IoT environments. What Is An Open Source Hypervisor? An open-source hypervisor is a virtualization software that lets you create and manage multiple virtual machines (VMs) […]
The Best Hypervisors
How To Choose The Best Hypervisor For Your Needs Define Your Workload Requirements Determine whether your workload demands high-performance, enterprise-grade virtualization or simpler, lightweight testing environments. Bare-metal hypervisors (Type 1) run directly on the hardware, offering optimal performance and reduced overhead, making them suitable for production-grade applications. Hosted hypervisors (Type 2) run on an existing […]
What is a Cloud Hypervisor?
A cloud hypervisor is a foundational technology in cloud computing, enabling the virtualization of hardware resources to create, manage, and operate multiple virtual machines (VMs) on a single physical system. It acts as a software layer that abstracts the physical hardware and provides isolated environments for running applications or workloads. By allowing multiple operating systems […]
What Is A Hypervisor? Everything You Need To Know
Virtualization has revolutionized IT, enabling businesses to optimize resources and streamline operations. At the core of this innovation is the hypervisor, a tool that facilitates the creation and management of virtual machines, transforming the way organizations handle computing workloads. Below, we’ll explain how hypervisors work, explain the differences between their types, and discuss key steps […]
The Best Small Business Firewalls
Firewalls are an important part of your network’s security and are often seen as the first line of defense. They sit at the edges of your network and analyze the incoming and outgoing traffic. Since the data travels in the form of packets, firewalls analyze their headers and sometimes, even their content. This information is […]
Troubleshoot Network Connectivity
Network connectivity issues are one of the most common problems for IT help desks today. It can occur due to a host of reasons and the fix will depend on what caused the issue in the first place. In this article, we will be looking at some possible causes of network connectivity issues and how […]
How to Configure Cisco Switches
Cisco switches provide outstanding performance, security, scalability, and cost-efficiency for any network type. They are not ordinary plug-and-play devices that do not need configuration or involvement when resolving issues. However, Cisco switches do require an initial setup, ongoing monitoring, and maintenance. How to configure a Cisco switch? In this step-by-step guide, we’ll configure a Cisco […]
Network Topology Guide: Types, Mapping, and Design
Networks have become ubiquitous in our world today. But do you know that networks can be of different types, mapping, and design to meet the specific needs of an organization or group using it? Well, in this article, we are going to take a deep dive into network topology and talk extensively on the pros […]
The Best CPU Temperature Monitors
Optimal temperature is essential for good health. This statement applies to living beings and computer components because they are designed to perform well only when the temperature is within a specified range. However, too much heat can damage your computer’s Central Processing Unit (CPU) and other components such as the motherboard, hard disk, etc. Now […]
How to Fix Packet Loss?
Every piece of information transmitted over the Internet is split into small packets, numbered, and transmitted. The receiving device receives these packets and constructs the message based on the numbering and other information present in the header of each packet. Sounds simple, right? In the real world, though, the packets can get lost en route […]
API Security Guide
You must have heard of the term “API,” but do you know what it means? The word “API” stands for Application Programming Interface. It enables two or more software to interact with each other and complement or leverage each others’ capabilities without knowing the intricate and code details of either software. In other words, the […]
The Best Data Center Monitoring Tools
Managing a data center is anything but easy given the multitude of systems and devices and the complexity of ensuring that each of these work at optimal levels always. Besides the software and hardware, an organization also has to ensure that the cooling units are correctly wired and are working fine. Such a mammoth list […]
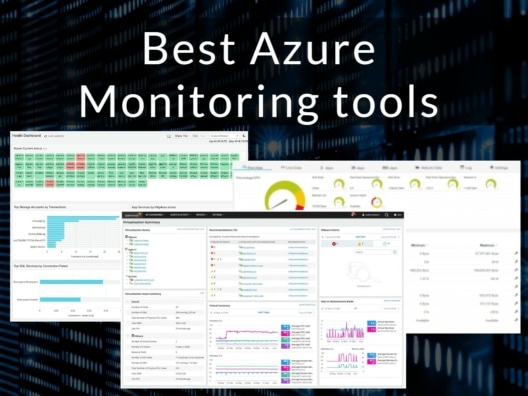
The Best Azure Monitoring Tools
Azure, the cloud computing service from Microsoft, can significantly enhance your organization’s productivity, collaboration, and ease of use. However, just like any other tool, it has to be well-managed and monitored to ensure that it is up and running at all times in optimal health. Here is our list of the best Azure monitoring tools: […]
The Best File Integrity Monitoring Tools
IT Security is a word that we keep hearing often as it encompasses a wide variety of systems, devices, networks, and a company’s IT infrastructure as a whole. In reality, though, this word is more talked about than implemented as is evident from the 2021 Cybersecurity Report that states that 21 % of files are […]
The Best Serverless Monitoring Tools
Monitoring has become an essential part of the IT infrastructure today, but have you ever wondered how monitoring happens for distributed applications over many functions and services? Add in agents and wrappers to the mix, and you have one of the most complex setups in the IT world. This is a unique challenge with the […]
SNMPwalk Examples for Windows and Linux
Digital communication appears instantly and seamless to us today, but many complex processes happen in the background. One such process that plays a big role in digital communications is the Simple Network Management Protocol or SNMP for short. This is an application layer protocol defined by the Internet Architecture Board to enable seamless communication between […]
How to Make an Access Control List (ACL)
The many security issues and breaches that we see today are mostly a result of incorrect entities accessing certain resources. So, only authorized users must have access to the required resources, so everyone is not accessing everything. There are many ways to implement this streamlined access effectively, and one of them is through the access […]
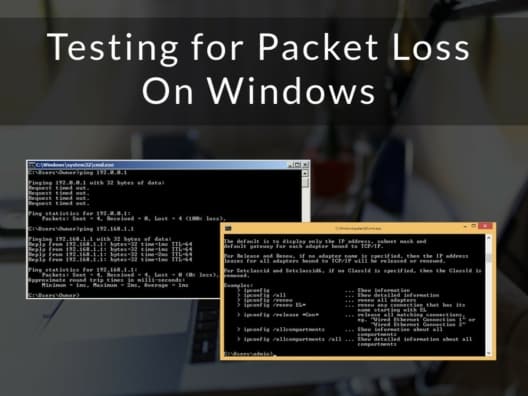
Testing for Packet Loss On Windows
Sending and receiving data from the Internet has become such an integral part of our lives that we don’t even think about the nitty-gritty details of how it is transported, until a problem comes up in the form of slow connections, dropped calls, or no response to your requests. When these problems occur, you’d want […]
The Best Web Application Firewalls
It is safe to assume that web applications come with security vulnerabilities that make them vulnerable to hackers. Research shows that in most cases cross-site scripting (CSS) is at fault, so it is important that you have a protection mechanism that will protect your application from this type of attack. Similarly, SQL injection and cookie […]