Accenture, in its 2019 Cost of Cybercrime Study, stated that Information theft is the fastest rising consequence of cybercrime and one of the primary reasons why organizations must invest in sound cybersecurity strategies to protect their data. According to the report, Malware and Web-based attacks are one of the most expensive cyberattacks. In fact, over the past few years, ransomware and malicious insider threats are dramatically expanding and become more complex.
If the attackers gain access to your crucial data, they can use it to identify fraud or as ransomware. Whether your data is in transit, motion, or at rest, it is always at risk of being seen by prying eyes if not protected.
Small and mid-size businesses are always the main target of cybercriminals for they lack sophisticated data security policies and tools. At the same time, it doesn’t mean that the larger enterprises are immune to the risk.
You cannot control the movement of attackers but can surely reduce the risk and chances of data theft by developing a proper strategy that will help monitor and secure your data at rest and in motion.
Here, we will discuss data at rest and the benefits of data at rest protection. Further, we will discuss how to secure data at rest from external and internal threats. Additionally, why companies need to develop and invest in sophisticated data security policies and tools.
Attackers can make a move at any time, hence, all organizations must prepare themselves beforehand to avoid financial damage and other consequences.
What is Data at Rest?
Data at rest is the inactive data stored on stable media, such as hard drives and tapes. Data stored in off-site backups, databases, and archives are also referred to as data at rest unless it is used or transported to another location.
Any data moving across a network is called data in transit, and similarly, the one stored in memory but is actively in use by a software program is known as data in use. However, the one that is stored and inactive is the data at rest.
Why You Should Protect Data at Rest?
No matter where data is traveling, effective measures for protecting this type of information are needed, as it is typically the most vulnerable type of data while it is traveling. Similarly, the Data in motion can also become a target when it travels. However, the data at rest is protected through the firm’s cybersecurity strategy and is typically stored on-premises on a firm’s network; it is still subject to threats, as the attackers try to access it with financial gain in mind.
Cybercriminals often aim for data at rest because it comprises some of the most crucial data and represents a bigger pay. Data stored in the cloud or on shared workstations are also at risk of being seen by prying eyes if not protected.
Earlier, data at rest was saved in an organization’s on-premise servers or local computers. But, as the companies started moving to the cloud, the same information was stored on remote servers. These servers are generally managed by external vendors, which is also a risk factor. Hence, each company must evaluate its providers’ cloud storage security measures and configurations.
Unprotected data at rest leaves enterprises open to attacks. For example, the data at rest in mobile devices are at a higher risk compared to other devices. Hence, it is crucial to secure Data at Rest using an integrated cloud security strategy, which includes strong encryption and a robust data analytics platform.
Benefits of Data at Rest Protection
Apart from providing increased security and privacy, inactive data protection also protects your stored data at rest content from unauthorized access.
Inactive data protection reduces the risk of unauthorized access, data theft caused by lost or stolen devices, inadvertent password sharing, etc., by using appropriate encryption and access control.
Encryption is a common solution used to protect data both at rest and in motion. This is why encrypting data at rest or in transit is just one of the many layers of security companies can use to protect their information. Encryption is the most effective way to reduce the chance of a security breach.
Data encryption at rest can protect your organization from unauthorized access to data when computer equipment is sent in for repair. Further, it protects data while it is stored on a mobile device, computer, tablet, data store, or cloud, including frequently used cloud services and corporate websites.
If your data falls into the wrong hands, the criminal will still not be able to access your data in full due to its encryption, and without an encryption key, your data remains protected.
Other benefits of data at rest protection include:
- Only authorized and trusted users can access data at rest.
- Allows performing extensive auditing that delivers better visibility over network data at rest.
- Prevents data at rest from insider attacks.
How to Secure Data at Rest?
Encryption plays an important role in protecting data and is a popular tool to protect data in both transit and at rest.
With the increase in cybercrime, investing in Data-at-Rest Security tools could be an excellent way to help secure data. Apart from practicing other security measures, organizations must invest in these tools to make sure those who have gained rogue access to your key management systems cannot gain access to your data.
Hence, to protect data from getting accessed or stolen, employ data encryption, password protection, or a combination of both security measures. These security measures ensure that the stored data is not vulnerable to hacking or other unauthorized access.
Enterprises must look beyond the different types of cloud security issues, which have been swallowing up data at rest.
Classify and Encrypt Data at Rest
Organizations must know where all the data resides and must classify it, and limit locations. One of the best ways to secure your data at rest is to store at limited locations and encrypt it. Also, they must know about the critical nature of their data and should classify it.
Classification helps companies to regularly re-evaluate the sensitivity levels of the stored data and improve/increase data protection as per the need. These classification methods may vary for each organization. But still, businesses must continue to assess and classify which applications or information are more crucial for business and how important a role they play from a business continuation perspective.
Let us say, if an application helps generate good profit and is beneficial to an organization in different ways, it’s likely to be important equipment for business continuation or growth. As a result, businesses must consider it to be crucial.
Organizations must constantly re-evaluate the stored data and its protection level. For example, once you labeled data as low-risk information but after a few months, after reassessing it turned out to be at high risk. Now, it requires immediate attention and changes to the process of encryption and policies managing encryption keys to avoid data theft.
As a result, your organization manages to protect itself from damage. Just keep in mind that the data at rest will remain secure as long as the infrastructure that supports it maintains proper security. Hence, businesses must also make sure that the servers, network hardware, and software on-premises or in the cloud are always protected.
Security Tools
One must invest in security tools or hire professionals that perform continuous monitoring of internal and external threats trying to access data at rest.
Employee Training
Also, organizations must train authorized employees about the importance of securing data at rest. In today’s time, data protection is crucial for every business. Hence, businesses must adopt sound cybersecurity strategies that prevent data loss or theft.
There are a few IT administrators that also get concerned over encryption as it might cause performance issues in a few cases. But, it does not mean you stop yourself from reaping the security benefits encryption provides. To reduce performance issues and protect data at rest, businesses can simply encrypt selective sensitive files before archiving and/or choose to encrypt the drive itself regardless of sensitivity.
As cybercriminals continue to develop more sophisticated methods to access and steal corporate information, encryption at rest has become a must for any security-conscious organization. Hence, even in some cases if it causes performance issues, a business must use data encryption methods to protect data at rest from theft and breaches.
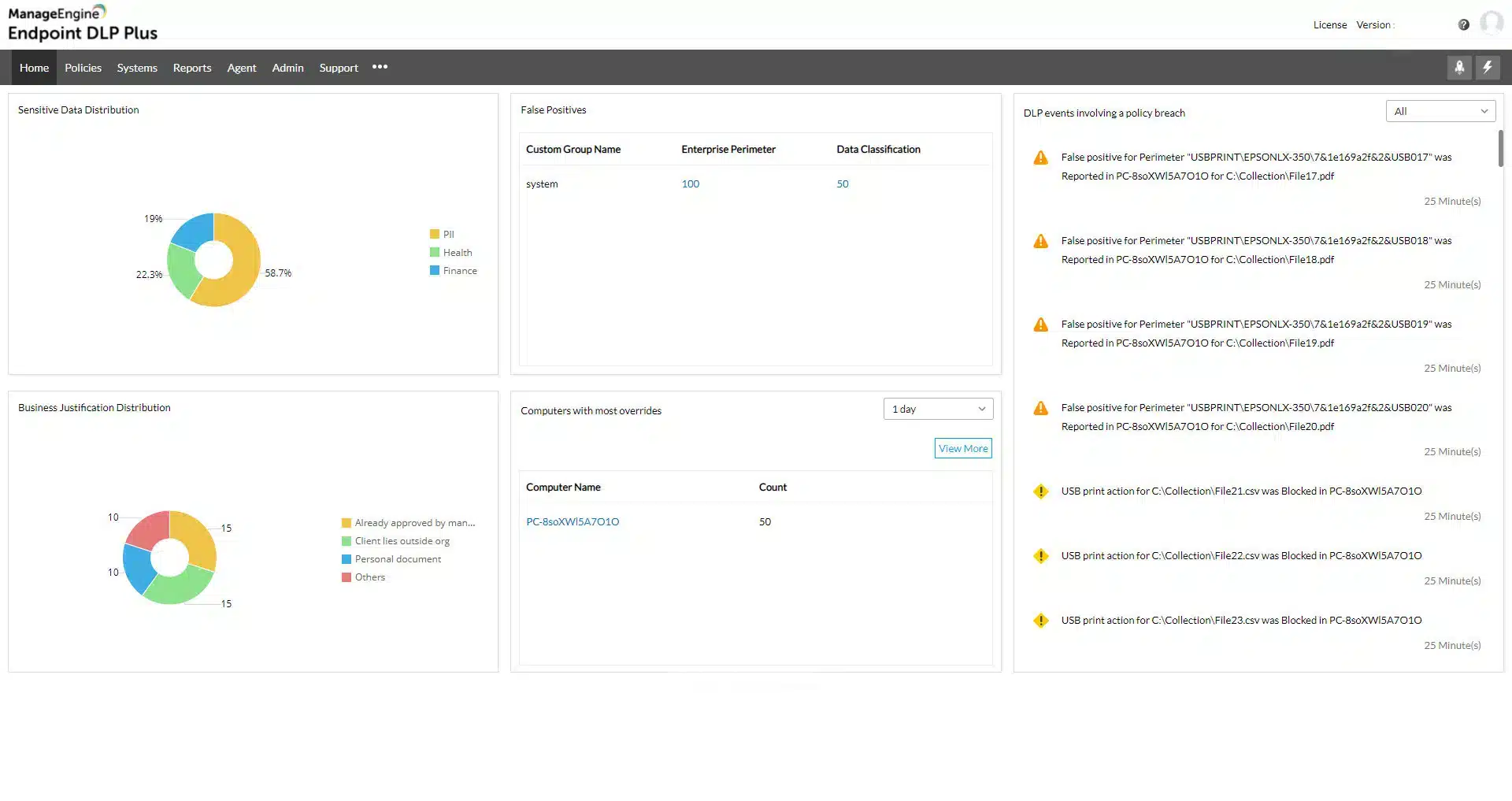
Protecting Data at Rest with ManageEngine Endpoint DLP Plus
Another option to consider is ManageEngine Endpoint DLP Plus. This tool is specifically designed to protect sensitive data. It has a data discovery module that will identify different types of sensitive data according to your specifications, which usually relate to a data protection standard, such as GDPR or PCI DSS. The search for data includes scans of images and results in a list of locations, which could be duplicates of the same data.
The system manager then has the option of reconfiguring the applications that access these data stores to move their default storage location to a central server or just leave them as they are and implement monitoring on many different locations. The system can also include cloud platforms in its scanning routines.
All files and their locations are logged in a register and when any new file is created or transferred onto the monitored system, Endpoint DLP Plus will scan it for sensitive data instances.
The protection system of Endpoint DLP Plus focuses on the applications that access the data stores. The tool blocks all untrusted software, forcing users to only use well-known systems, such as Microsoft Office, which the administrator should ensure requires access credentials.
In order to block user attempts to bypass access controls by moving a file off the endpoint so that it can be amended elsewhere, Endpoint DLP Plus blocks USB ports, access to printers, and file transfer systems.
The administrator can then selectively approve any of these channels for use by a specific user. The Endpoint DLP Plus system also includes a reverse firewall to scan outgoing file transfers and emails for sensitive data instances and it will block those movements if they are not specifically authorized.
Endpoint DLP Plus installs on Windows Server and ManageEngine offers it in free and paid editions. The Free package has the same features as the Professional edition but it is limited to managing data on 25 endpoints. You can get the Professional edition on a 30-day free trial.
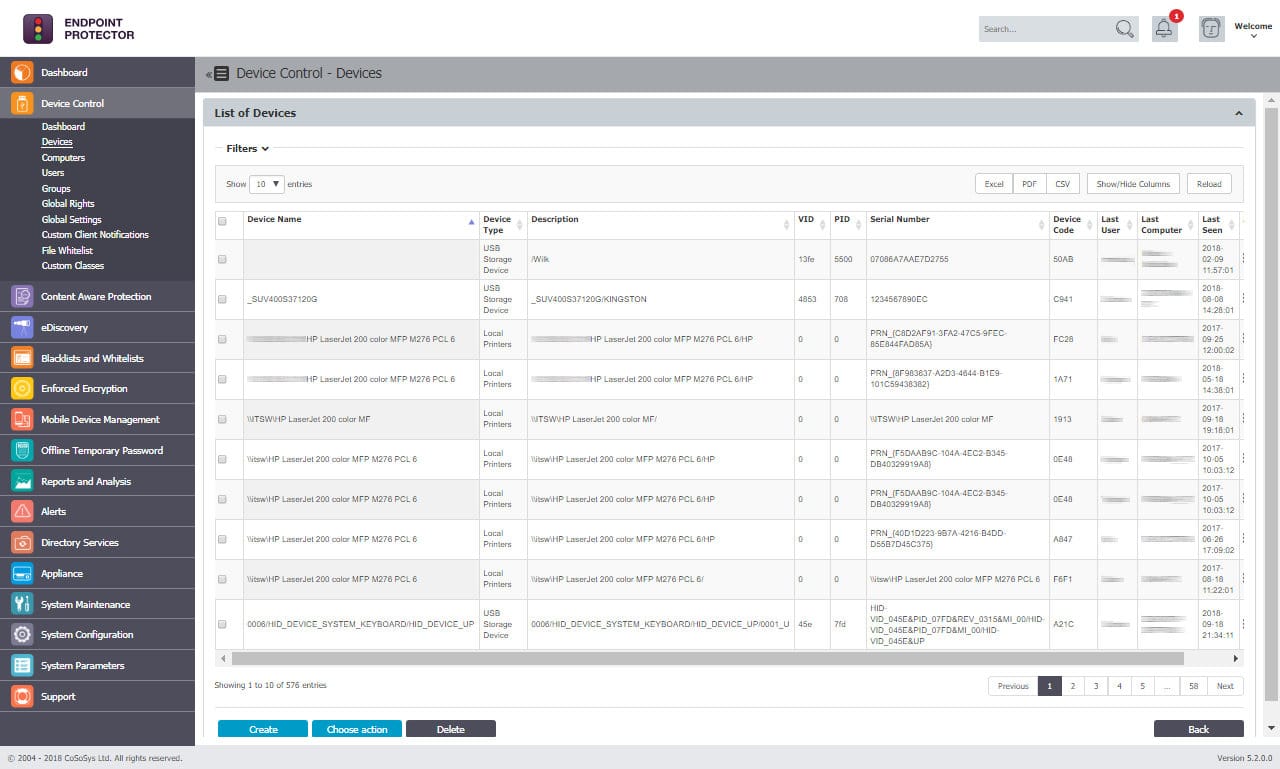
How Can You Protect Data at Rest with CoSoSys Endpoint Protector?
No doubt, data protection has become a top priority and each organization must develop the right cybersecurity strategies to overcome fraud and breaches. Businesses need to measure every angle and plan a strategy that would protect their data in transit, motion, and at rest.
Today, many high-profile companies like Allianz, ING, Samsung, Western Union, etc., trust Endpoint Protector by CoSoSys for data at rest protection.
It is because it is fast and supports various advanced technologies that help monitor and protect data in transit or at rest. At the same time, it maintains regulatory compliance with HIPAA that governs healthcare information, and standards like PCI-DSS are responsible for protecting credit card numbers, GDPR, SOX, etc.
CoSoSys Endpoint Protector is one of the best Data Loss Prevention (DLP) solutions that secures data at rest and blocks mobile devices, or removable storage drives from detecting any suspicious activity. This way the tool protects cyber attackers from accessing sensitive or crucial data of your business.
The DLP solution also offers enforced encryption features and prevents data exfiltration. It provides lightweight agents to protect your sensitive data throughout the entire network. No matter which device you run or where you have stored your crucial data, CoSoSys Endpoint Protector provides full protection and ensures compliance with regulations.
It also supports a reporting and analysis tool that helps businesses monitor every activity and prevents leakage.
You cannot avoid data at rest as attackers often target such data and resell it on the dark web to gain better profits. It is therefore essential that companies invest in a security tool like CoSoSys Endpoint Protector that prevents inadvertent and malicious leaks of valuable data stored in hard drives and tapes.
It also supports eDiscovery features that enable businesses to scan and identify all confidential data and perform encryption and decryption operations without causing any impact on its performance.
Further, it allows only authorized individuals to gain control over data.
Hence, CoSoSys Endpoint Protector is a cross-platform DLP solution that protects all your Personally Identifiable Information (PII) stored on different endpoints.