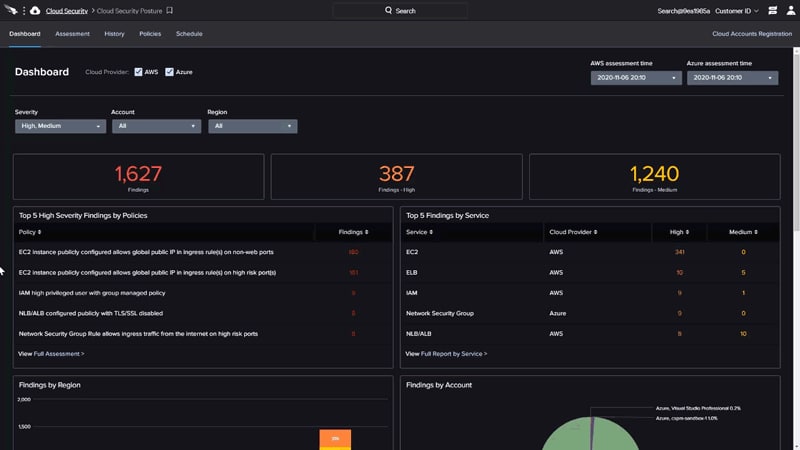
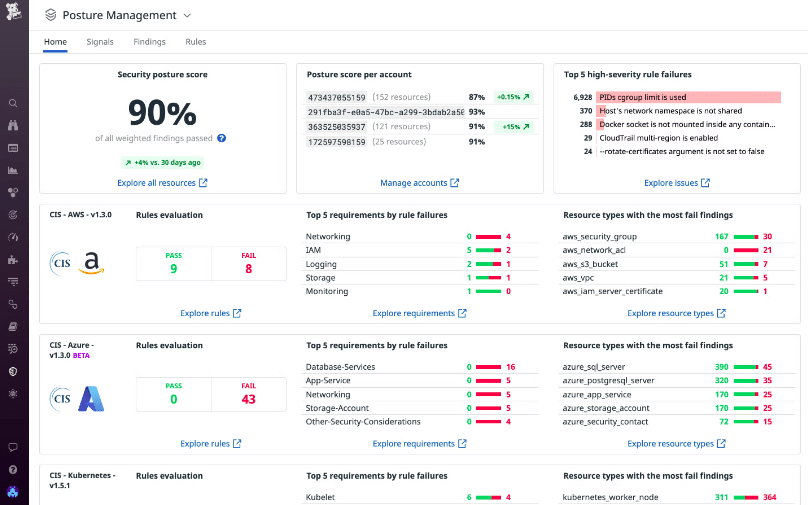
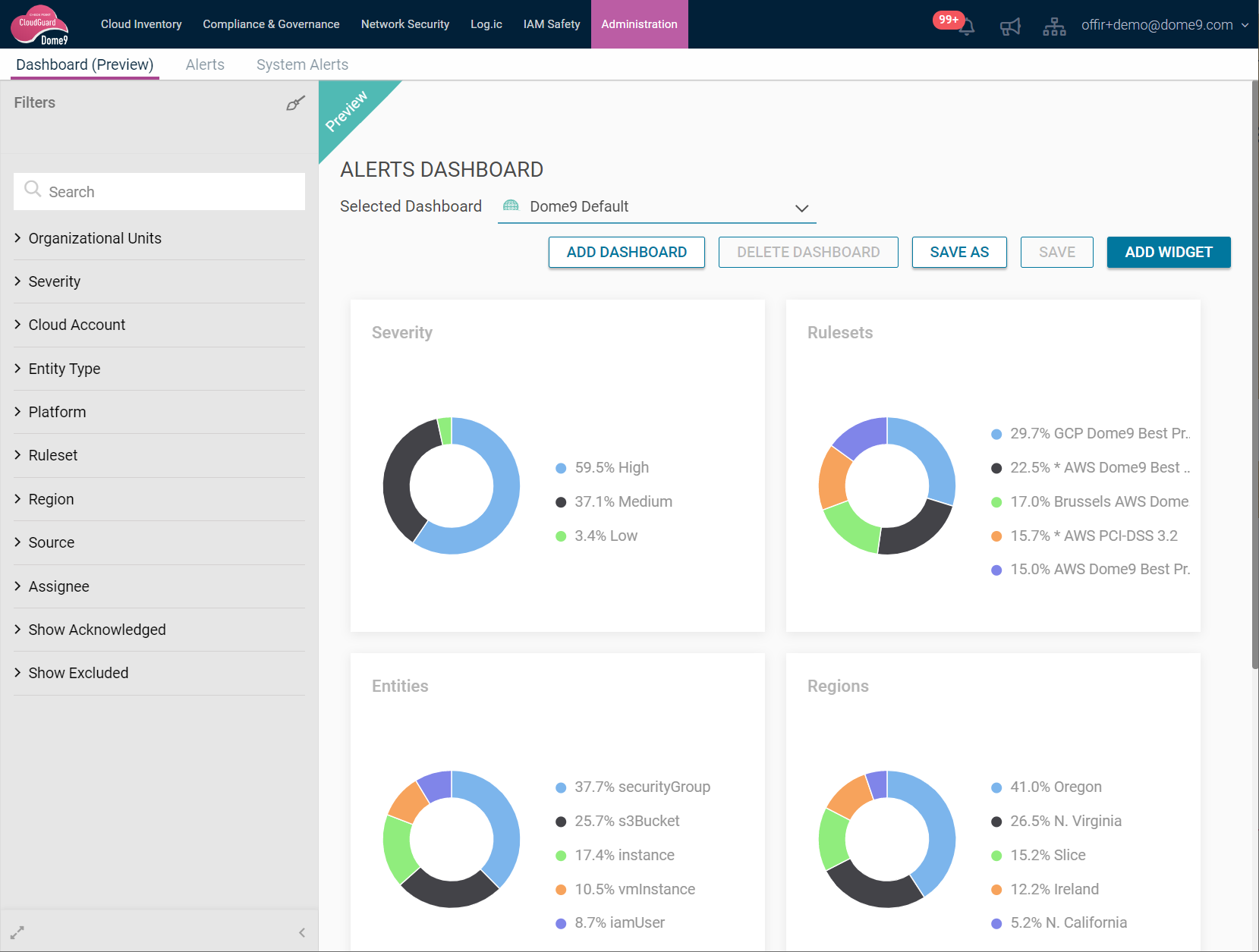
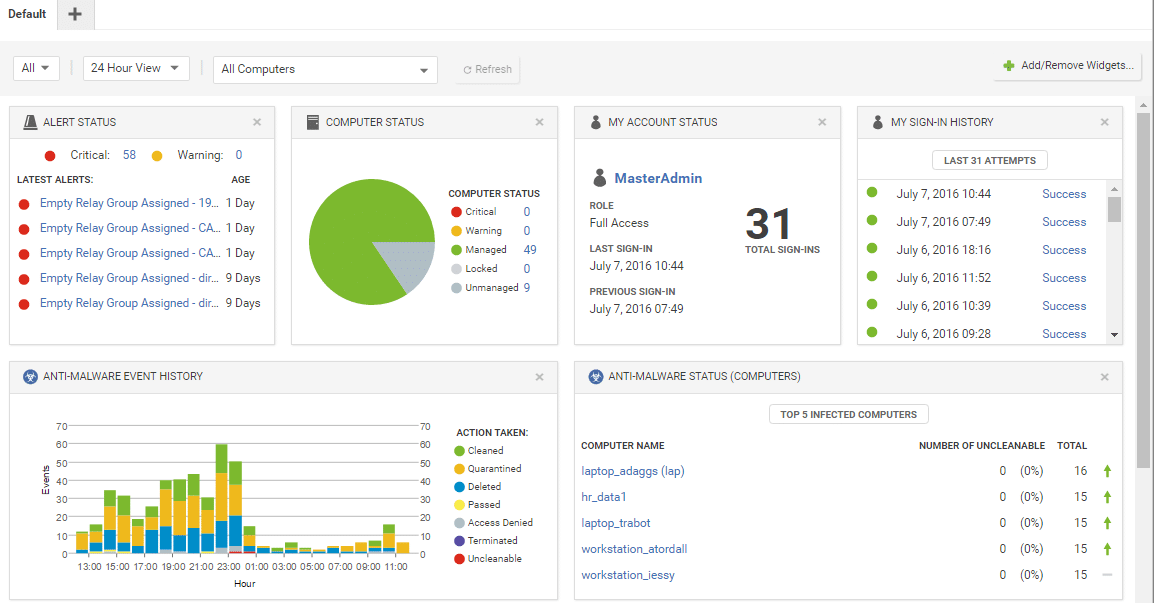
With the advancement in technology, most enterprises are moving to digital platforms for better performance and reach. A cloud connects with multiple networks daily, which makes it more powerful and useful for enterprises to run and expand their business. However, there are also various cybersecurity challenges in the cloud that demand a secure cloud-based system.
To identify compliance risks across the cloud infrastructure, Cloud Security Posture Management (CSPM) tools were introduced in the market. Here, we will discuss CSPM tools, their features, importance, and things to consider when buying IT security tools for the enterprise. Also, we have shortlisted some of the best CSPM tools available in the market that can be beneficial for your enterprise.
Here is our list of the best CSPM tools:
- CrowdStrike Falcon Horizon This CSPM provides system security assessments for resources hosted on AWS, Azure, and Google Cloud Platform.
- Datadog Cloud Security Posture Management This service continuously scans cloud assets for security weaknesses and produces compliance auditing.
- Check Point CloudGuard A package that combines CSPM and workload protection and is suitable for development as well as live system monitoring.
- Trend Micro Cloud One Protects on-site systems plus cloud resources hosted on AWS, Google Cloud Platform, and Azure.
- Aikido This SaaS platform implements security testing for applications under development and that includes a CSPM that ensures the cloud systems that will host the new system.
- BMC Helix Cloud Security This SaaS package scans cloud assets for security weaknesses, fixes them, and documents everything for compliance reporting.
- Lacework This cloud platform extends its security assessments of cloud resources to access rights management and also provides risk prioritization.
- Threat Stack Cloud Security Platform With this platform of security systems, you get ongoing security monitoring as well as vulnerability assessments.
- Palo Alto Prisma Cloud This service focuses on cloud storage systems and the access permissions operating on them, plus it provides compliance logging.
What is Cloud Security Posture Management?
CSPM are security tools designed to discover misconfiguration issues and remediate risks across the diverse cloud infrastructure ((Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS)). The main reason behind designing the powerful tool was to monitor the diverse cloud infrastructure on a continuous basis for security gaps, risk visualization, and assessment.
The term CSPM was coined by Gartner to help automate security in the cloud using a set of security products. These security products also had the capability to examine public and private clouds against the defined practices and provide compliance assurance. Also, most of the tools have features like an alert system to update cloud customers about the security risk and how to remediate them. While the sophisticated ones prefer Robotic Process Automation (RPA) features to automate remediation.
It is one of the best choices for enterprises that wish to secure hybrid cloud and multi-cloud environments. In most cases, it is used by organizations to discover misconfiguration issues and eliminate compliance risks across PaaS cloud environments, SaaS, and IaaS.
Features of Cloud Security Posture Management Tools?
CSPM tools perform continuous monitoring and include some of the advanced features that enable automatic detection of configuration mistakes without any delay or human intervention.
Here are some of the other key features of CSPM tools:
- Automates identification and remediation of misconfiguration issues in the cloud
- Uses best practices to detect cloud configurations and other issues
- Maintains consistent enforcement across all cloud environments
- Offers policy visibility
- Instance scanning for misconfigurations
- Conducts risk assessments
- Storage bucket monitoring
- Mapping of configuration statuses to security control framework
- Compatible with hybrid and multi-cloud environments
- Automates remediation of risk across all cloud infrastructures, including SaaS, IaaS, and PaaS platforms
- Monitors encryption and account permissions
- Conducts analysis over data resources in different environments
- Provides real-time visibility
- Generates audit-ready reports for analysis
- Provides protection against threats
- Delivers quality insights into potential compliance risks
- CSPM tools allow monitoring the creation of new instances
Why You Need Cloud Security Posture Management Tools?
Misconfigurations in the cloud are common, but with the help of CSPM, one can secure the cloud environment and reduce the risk of data breaches.
A cloud connects with multiple networks on a daily basis. It increases the risk of cyberattacks. Thus, to protect and secure cloud-based systems, investing in CSPM tools is the right thing to do.
The security tools provide unified visibility across multi-cloud environments, which helps prevent the data from accidental vulnerabilities and misconfigurations. Also, the administrators can monitor, scan, and assess the environment on a continuous basis and uncover hidden threats.
Further, it helps reduce alert fatigue, i.e., the false positives using artificial intelligence.
Things to Remember Before Choosing Cloud Security Posture Management Tools
There are various factors one must always consider when selecting a CSPM tool. Have a look!
- Company’s requirement Discover the key problems and prioritize your requirements from the company’s point of view. Think and analyze all the vulnerable areas of your organization and cloud environment before investing in a new tool. Go through a number of tools and then select the one that suits your business needs.
- Look for the Advanced Features Automatic configurations, monitoring capabilities, etc., are a few advanced features that play a vital role and must be taken into consideration before picking a tool for your organization.
- Details about Pricing Do not miss on thinking about your budget. You can find various tools online that offer advanced features at a low price. Instead of investing in an expensive tool with similar features, it is best to invest in a tool with adequate prices. Go through the plans and pricing of each tool before making a final call.
- Free Trial Session Availability Many tools offer free trial features, including the necessary resources that are required to start the procedure. It is best to look for such tools, and check if the team members find them sufficient enough to commence the process. It can also help you analyze the tool and switch if necessary.
The Best CSPM Tools
Methodology for Selecting the Best CSPM Tools
Choosing the best CSPM tool for your organization is a critical decision. The right tool can help you automate security processes, streamline operations, and reduce costs. Here, we will provide a methodology for selecting the best CSPM tool:
- Check if it offers automated remediation and can discover underlying services
- Does it provide instant alerts on discovering issues?
- CSPM activity logging is available or not?
CSPM tools are highly advantageous for any organization as they offer around-the-clock monitoring, automated detection features, and full visibility of security posture. Thus, protecting the organization’s crucial data safe from threats and vulnerabilities. Have a look at some of the top CSPM tools that can protect and secure cloud data.
1. CrowdStrike Falcon
CrowdStrike Falcon is a great choice to ensure that your company’s crucial data remains secure. It is a popular cloud-based endpoint protection solution that detects and prevents misconfigurations and ensures compliance across multi-cloud environments.
Key Features
- Lightweight and fast CSPM tool
- A lucid tool that offers high-level protection and efficiency
- Threat detection
- Identification and monitoring data breaches
- Reduces security blind spots
- Enforce permissions
- Supports seamless integration with SIEM solutions
- Access valuable context and insights
- Provides suggestions to prevent future security incidents
- Provides visibility into multi-cloud environments
- Constant monitoring of cloud resources
- Provides details automatically upon deployment
- Full control
- Reduces alert fatigue
- 50+ IOA detections
- Eliminates compliance violations
Why do we recommend it?
CrowdStrike Falcon stands out for its lightweight design and multi-cloud environment visibility, offering endpoint protection that rapidly detects and prevents misconfigurations. Its features like reduced alert fatigue and actionable prevention suggestions make it one of the top choices in cloud security.
CrowdStrike Falcon is a fast and lightweight CSPM tool equipped with an endpoint detection capability. Using these tools, users can gain access to complete visibility across AWS, Azure, and Google Cloud. Further, it provides suggestions to developers and helps them avoid costly mistakes.
Get insights into the overall security posture using CrowdStrike Falcon. Another advantage of investing in CrowdStrike Falcon is its API enables users to easily connect with various security solutions.
It supports multiple prevention features that help detect malware and fight off new techniques that cybercriminals come up with. Furthermore, the CSPM tool’s cloud-based architecture allows it to turn operational in minutes.
Who is it recommended for?
CrowdStrike Falcon is recommended for enterprises that need an agile, cloud-based endpoint protection solution, especially those operating across AWS, Azure, and Google Cloud. It’s particularly beneficial for development teams needing real-time monitoring and guidance to avoid costly errors, as well as organizations concerned with compliance.
Pros:
- Helps discover security loopholes and known targets of different hacking groups
- Examines system configurations as well as primary assets
- Groups cloud asset monitoring across different platforms
- Allows users to check virtual networks and containers
- Offers compliance reporting and remediation guide
Cons:
- Need to work on the migration part
- Device group configuration can be a bit more intuitive
You can register for a 15-day free trial.
2. Datadog
Datadog is a trusted CSPM tool that provides continuous monitoring and scanning of containers, hosts, accounts, and network performance. With Datadog, you do not require any additional agent as it has a unified Datadog Agent. The security tool also features deep observability capabilities that help users to identify, discover, monitor, and respond to threats.
Key Features
- Continuous scanning configurations
- one-click security posture monitoring across your infrastructure
- Full Visibility into configuration status
- Instant threat response
- Configuration monitoring
- Monitors cloud accounts, hosts, and containers
- Insightful reports
- Installs in minutes
- Timely notify about configuration alerts
- Provides alerts about potential misconfigurations and violations
- Scale efficiently
- Data aggregation
- Supports container monitoring
- 500+ integrations
- Distributed tracing
Why do we recommend it?
Datadog excels in providing continuous monitoring and scanning across multiple layers of your infrastructure, from containers to cloud accounts. Its deep observability features and wide range of integrations make it a powerful tool for both threat detection and configuration management.
With the help of Datadog, administrators can keep a track of incoming threats that are hidden in the cloud instances and containers. Another feature that makes it different from the rest security tools is that Datadog supports 600+ integrations and hardly takes any time to install.
Users can also monitor the threat movement in real-time, track security posture scores across your infrastructure, and perform continuous configuration checks. If you are looking for a security tool that helps detect threats quickly and helps identify misconfigurations and suspicious files in real-time, look no further.
Who is it recommended for?
Datadog is well-suited for organizations that require real-time monitoring and reporting across a diverse set of cloud environments. It’s particularly beneficial for compliance-focused businesses that need to adhere to standards like HIPAA and GDPR, as well as teams looking for extensive integration options.
Pros:
- Datadog Cloud Security Posture Management offers compliance reporting to HIPAA, GDPR, etc.
- Quickly discover any alteration made to cloud service settings.
- Even non-technical users can use the tool
- Automatically logs its findings and records any corrections
- Send immediate alerts on discovering any misconfiguration
Cons:
- Automated remediation is not available
- It might be difficult to navigate new places.
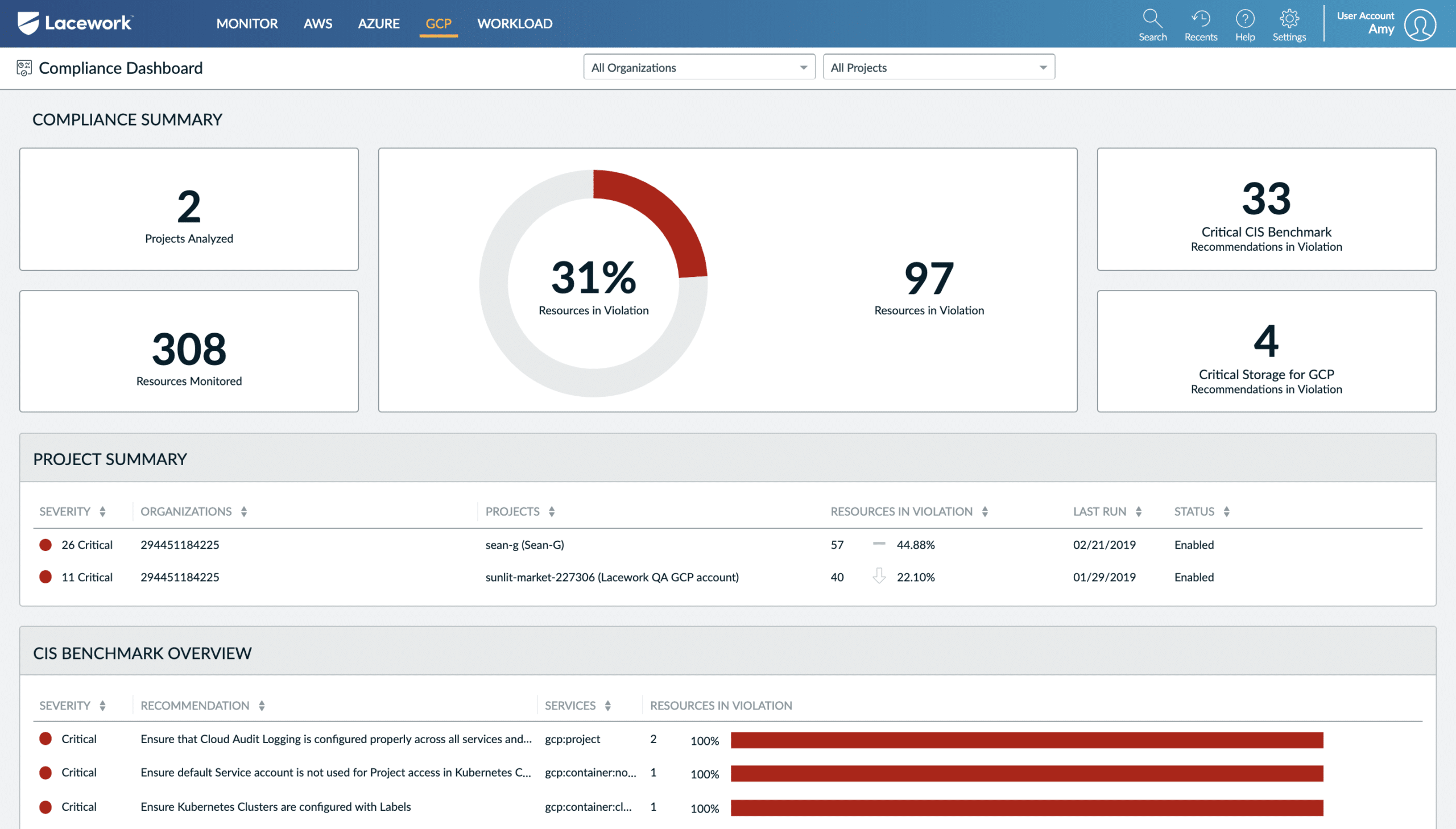
3. CloudGuard Posture Management (Dome9)
CloudGuard Posture Management helps visualize your security posture, and automates governance and compliance across multi-cloud services. It is another trusted security tool that helps detect misconfigurations, vulnerabilities, and threats. Further, it enforces best security practices and policies across different projects, accounts, and virtual networks to protect your sensitive data.
Key Features
- Automates governance and compliance
- Enforcement of gold standard policies
- Visualization of security posture
- Access to prioritize and auto-remediate events
- Comprehensive reporting
- Offers high-fidelity visibility
- Customizable policies
- Access control
- Data discovery
- Supports Identity Access Management (IAM) roles
- Performs audits to detect irregular activities
- Cloud intrusion detection
- Protects from insider threats
- Provides real-time alerts
- Offers workload protection and application security
- Secures cloud assets and spots potentially unauthorized activities
- Threat intelligence feeds
Why do we recommend it?
CloudGuard Posture Management offers a robust suite of features, from automating governance and compliance to providing high-fidelity visibility into your security posture. Its capabilities for real-time alerts and auto-remediation make it one of the strongest contenders for cloud security solutions.
CloudGuard Dome9 also allows users to scale across different cloud platforms, including Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). It is an innovative service that protects your company’s data against insider threats.
Another reason for adding the CSPM tool to the list is CloudGuard Dome9 is a fast and effective cloud security platform that provides pain-free compliance and governance. CloudGuard Posture Management offers control over IAM users and roles, thus allowing administrators to find it easy to manage granular permissions across multi-cloud environments.
Who is it recommended for?
This tool is particularly useful for organizations that are operating in multi-cloud environments like AWS, Azure, and GCP, and require strict compliance and governance. It’s also an excellent choice for businesses concerned about insider threats and those in need of granular access control over IAM roles.
Pros:
- Offers Cloud Workload Protection and Application Security
- Helps keep a track of account takeover attempts
- Offers threat detecting and prevention
- Discovers configuration management issues and alerts immediately to administrators
- Offers continuous monitoring and cross-platform scanning
Cons:
- On-premises systems are not covered by the tool
- Check Point CloudGuard is a bit expensive for some users
4. Trend Micro Hybrid Cloud Security Solution
Trend Micro Hybrid Cloud Security Solution is an all-in-one solution that helps the organization meet all cloud security needs. It is a flexible and unified cloud security solution that detects threats, misconfigurations and secures cloud infrastructure.
Key Features
- Flexible cloud security migration
- Automates deployment and discovery
- Supports direct integration into users’ DevOps processes
- Provides full protection to cloud environment
- Offers timely detection and instant protection
- Offers visibility
- Supports a Single security management console to detect threats for all environments
- Broad APIs
- Accelerates streamlined compliance
- Supports endpoint and mobile threat protection capabilities
- File storage security
- Container security
- Server security
- Performs real-time analysis
- Automated policy management
- Provides 24/7 Managed Detection Response (MDR) service
- It helps uncover Indicators of Compromise (IoC)
- Integrates with AWS, Microsoft Azure, VMware, and Google Cloud
Why do we recommend it?
Trend Micro Hybrid Cloud Security Solution stands out for its flexibility, offering a unified approach to securing various cloud infrastructures. With features like automated deployment and 24/7 Managed Detection Response, it delivers robust and timely protection against threats and misconfigurations.
Its security services are not only restricted to cloud platforms but also support integration with users’ DevOps processes and AWS, Azure, Google cloud toolchains.
Get more visibility and save time using its automated deployment and discovery features. Today, many organizations are using this powerful CSPM tool to embrace a DevSecOps culture and build better architecture in the cloud.
The Trend Micro Hybrid Cloud Security solution has a single security management console that helps detect threats for all environments and protects various physical, virtual, and cloud servers.
Who is it recommended for?
This tool is particularly beneficial for organizations that are transitioning to or operating in multi-cloud environments such as AWS, Azure, and Google Cloud. It is also highly recommended for teams adopting a DevSecOps culture, needing a single console for threat detection across physical, virtual, and cloud servers.
Pros:
- Users can detect misconfigurations and threats faster
- Supports integration with Azure, Google cloud toolchains, and other DevOps processes
- Offers automated deployment and discovery that helps save time
- Offers better visibility and allows users to run real-time analysis
- Detects threats in real-time and secures physical, virtual, and cloud servers.
Cons:
- Response time and issue resolution from support is quite slow.
- Upgrades may halt as a result of some technical issues.
5. Aikido
Aikido is a cloud-based application testing package that includes infrastructure assurance systems. The processes for testing vulnerabilities in supporting systems include a CSPM for examining the security of cloud platforms and services.
Key Features:
- Automated Web application security testing – both dynamic and static
- Software composition analysis that examines the third-party components used in development projects
- Scans Infrastructure-as-code, containers, and Kubernetes cluster settings
- Cloud services security assessments with a CSPM
- Examines the security of runtimes running with containers
- Checks the configurations of cloud accounts
- Scores platform services for risk
- Aimed at DevOps teams that produce and manage Web applications and SaaS packages
- Includes assessments from CloudSploit and AWS Inspector
- Provides a severity score that prioritizes issues
- Deduplicates security errors, grouping them to prevent excessive error notifications
- A system that can fix some security errors automatically
- Integrates into CI/CDC pipelines
- Reports problems through bug trackers
- Automates compliance reporting for SOC 2 and ISO 27001
- Recommends tightening user permissions
Why do we recommend it?
The Aikido system scans cloud services that are going to be used to form part of a SaaS package or a Web application. The tool ensures that the services are properly configured and that their user account settings are kept secure. The service can fix some security weaknesses automatically.
The Aikido platform provides software composition analysis for components that developers want to include in their new applications. It implements continuous testing by triggering its dynamic application security testing and static application security testing off a new check-in at an enrolled repository.
IaC, container, Kubernetes, and cloud platform security scanning operated at the end of the development process and pertain to delivery and hosting services.
So the CSPM of Aikido is an element in the chain of security testing services that the creators and managers of SaasS platforms and Web applications need.
Who is it recommended for?
This service is designed for use by businesses that develop and run cloud-based systems, either for their own use or as commercial products for use by other companies. Aikido is offered as a SaaS platform with a subscription rate. Small developers would be interested in the Free edition.
Pros:
- Security testing that can be integrated into CI/CD pipelines
- Generates a severity score for each identified security issue
- De-duplicates errors that are related or multiplied in order to reduce the number of notifications that need to be dealt with
- Automatic fixes for some security issues
- User account settings assessments
Cons:
- This CSPM is part of a wider application security management platform and not a standalone service
Access the free plan to test the Aikido system.
6. BMC Helix Cloud Security
BMC Helix Cloud Security is an agile CSPM tool that automates configuration checks and remediation across multi-cloud environments, IaaS, and PaaS resources. Users need to perform no coding for automated remediation. The popular security tool is designed for both cloud and on-premise-based infrastructure.
Key Features
- Automates configuration checks
- Automated remediation for cloud Iaas and PaaS
- Cloud security scoring
- Provides ready-to-use policies like CIS, GDPR, and PCI
- Supports cloud advancement tools for updating user data
- Supports custom policies
- Anomaly detection
- Container configuration security
- Offer seamless integration
- Perform blind-spot detection and audit assessments
- Allows automated ticketing enrichment using ITSM integration
- Supports Integration to CI/CD pipeline
- Provides visibility into complex infrastructures
- Change management
- Alerts Option
- Insightful reports
- Allows scanning of the entire infrastructure
- Map dependencies among on-prem, multi-cloud environments
Why do we recommend it?
BMC Helix Cloud Security excels in automating configuration checks and remediation across multi-cloud, IaaS, and PaaS resources. With features like cloud security scoring and ready-to-use policies like CIS, GDPR, and PCI, it offers both speed and compliance in cloud security management.
It supports advanced analytics and tracking tool that helps detect threats and enable organizations to improve productivity and strengthen security.
BMC Helix Cloud Security tool further simplifies all the patching-related processes and offers great speed and security. Using BMC Helix, administrators can also gain visibility and access to software, service dependencies, and hardware across different clouds.
Another advantage of selecting BMC Helix Cloud Security over other CSPM tools is users can perform quick asset discovery and map dependencies of multiple devices and applications.
BMC Helix Cloud Security is an agentless, lightweight, and scalable security tool that performs blind-spot detection and audit assessments to discover vulnerabilities and out-of-date software.
Who is it recommended for?
This tool is a strong fit for organizations requiring automated, code-free remediation across multi-cloud environments as well as IaaS and PaaS platforms. It is also highly beneficial for businesses with complex infrastructures, needing seamless integration into ITSM and CI/CD pipelines.
Pros:
- Helps identify and fix setup issues across IaaS, PaaS, and multi-cloud systems automatically.
- No coding is needed for automated remediation
- Help map dependencies of several devices
- Runs audit assessments and helps detect blind spots
- Provides access to advanced analytics and tracking tools that help strengthen security
Cons:
- Development testing is not included
- The web interface will occasionally crash
7. Lacework
Lacework is another Cloud Security Platform with an automated and scalable architecture that delivers complete cloud security and compliance across AWS, Azure, GCP, and private clouds. Also, the security tool provides full visibility into cloud infrastructure, workloads, and containers.
Key Features
- Insightful reports
- Security configuration audits
- Detects threats, suspicious activities, and misconfigurations
- Offers faster deployment
- Scalable architecture
- Audit management
- Risk management
- Incident management
- Container scanning
- Vulnerability management
- Performs continuous tracking
- Adapts documented best practices
- Intrusion detection
- AWS security monitoring
- Workflow management
- Cloud gap analytics
- Security Auditing
- Access control
- Enables administrators to prioritize risks
- Infrastructure as code security
- Allows users to perform container and cloud workload analysis
- Behavorial analytics
- Simplified posture and compliance
Why do we recommend it?
Lacework stands out for its automated, scalable architecture and machine learning analysis features that allow for rapid detection of threats and vulnerabilities. Its capability to offer full visibility into cloud infrastructure, workloads, and containers makes it a comprehensive cloud security solution.
Using its in-built machine learning analysis feature, administrators can faster discover, detect, and monitor threats and vulnerabilities in the cloud. Further, Lacework delivers contextual data covering all configuration problems and the latest updates.
Nextdoor, VMware, FuboTV, snowflake are a few trusted supports of the popular Cloud Security Platform. It helps discover threats, vulnerabilities, misconfigurations, and unusual activity across the entire multi-cloud environment with its advanced features.
Who is it recommended for?
This tool is ideal for organizations utilizing multi-cloud environments, including AWS, Azure, and GCP, who require continuous threat and vulnerability tracking. It is also well-suited for businesses looking for detailed, insightful reports and a scalable security architecture that adapts to growing needs.
Pros:
- Provides compliance for private clouds, AWS, Azure, and Google Cloud Platform.
- Offers full visibility into workload and containers
- Helps detect threats and monitor cloud vulnerabilities
- It has a scalable architecture and provides fast deployments
- Constantly tracks and generates insightful reports
Cons:
- The Web GUI and product support require improvement
- Must work on alert handling
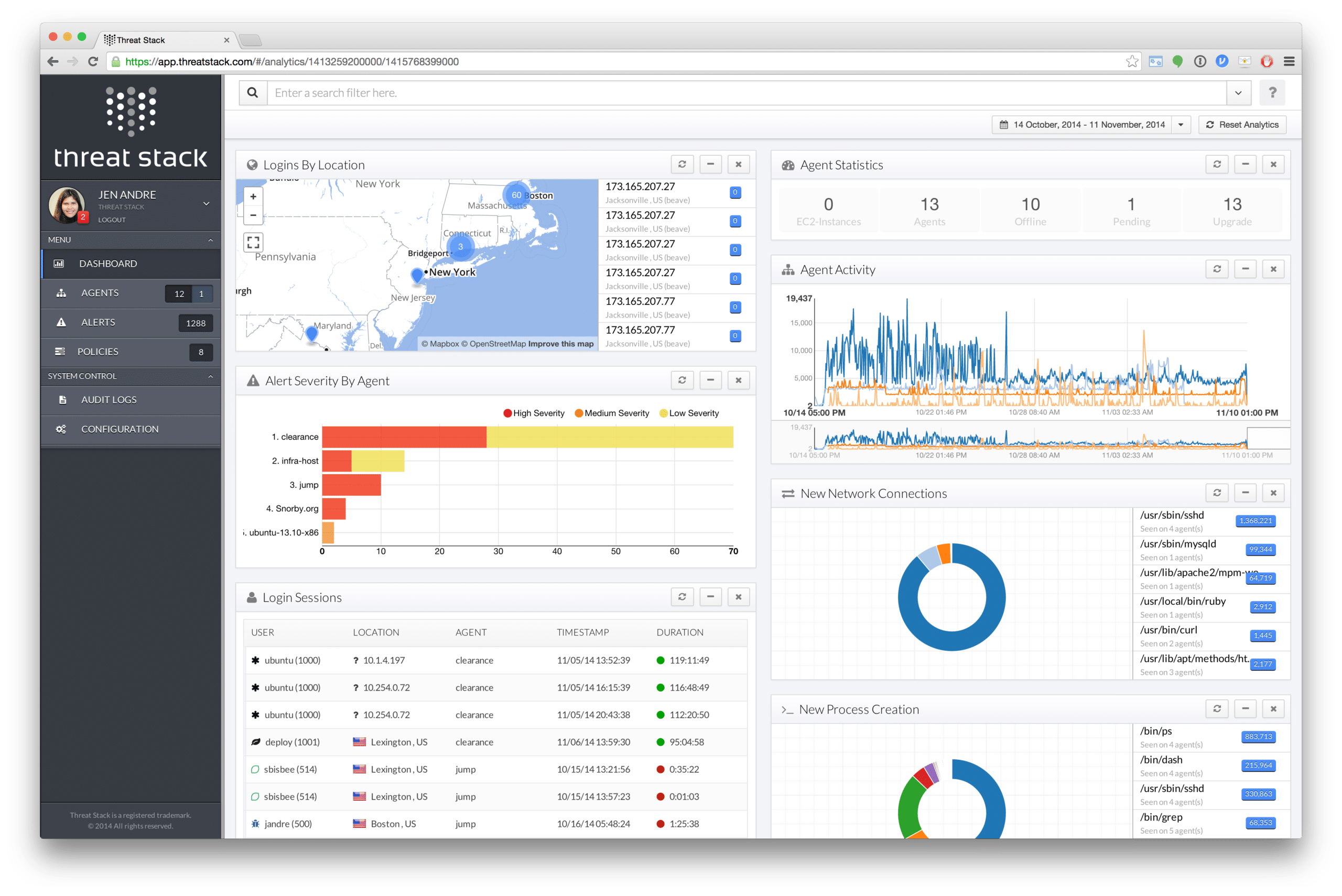
8. Threat Stack
Threat Stack is a CSPM tool designed for modern Apps and Cloud-Native Infrastructure that facilitates visibility across cloud management consoles, applications, and infrastructure. It is a popular cloud-based platform that helps businesses discover, prioritize, and respond to both real-time and unknown threats.
Key Features
- CloudTrail monitoring
- Application infrastructure protection
- Supports IAM policies
- Visibility to servers and cloud instances
- Configuration auditing
- EC2 inventory
- Configurable rules and alert system
- Vulnerability assessment
- Cloud gap analytics
- File Integrity Monitoring
- Intrusion detection
- Compliance tracking
- Incident management
- HIPAA compliant
- Policy management
- Advanced analytics
- Provides security and compliance across the entire cloud infrastructure
- Integrates with third-party SecOps tools
- Provides security to containers & Kubernetes
- Anomaly detection
- Real-time monitoring
Why do we recommend it?
Threat Stack excels in providing real-time visibility and actionable insights across cloud management consoles, applications, and infrastructure. Its robust set of features, including CloudTrail monitoring and IAM policy support, equip businesses to respond to both known and unknown threats effectively.
Also, it provides customers better results via its key capabilities and advanced features like Policy Management, Configuration auditing, Vulnerability Assessment, Incident Management, etc.
Threat Stack follows a unique approach to secure clouds using machine learning, rules, and combining full-stack telemetry. It is one of the best Application infrastructure protection tools that also support CloudTrail monitoring and IAM policies. If you are looking for a CSPM tool that responds to both known and unknown vulnerabilities and threats, then Threat Stack is a good solution for your business.
Who is it recommended for?
Threat Stack is a suitable choice for businesses operating modern apps and cloud-native infrastructures who prioritize real-time threat detection and response. It would particularly benefit organizations needing HIPAA compliance or those integrating with third-party SecOps tools.
Pros:
-
- Allows for insight across cloud management interfaces, apps, and infrastructure
- Users can prioritize and respond to threats in real-time
- Supports IAM policies
- Offers CloudTrail monitoring and Cloud Gap Analytics
Cons:
- Compliance needs attention and improvement
- Generates fewer insights into security groups
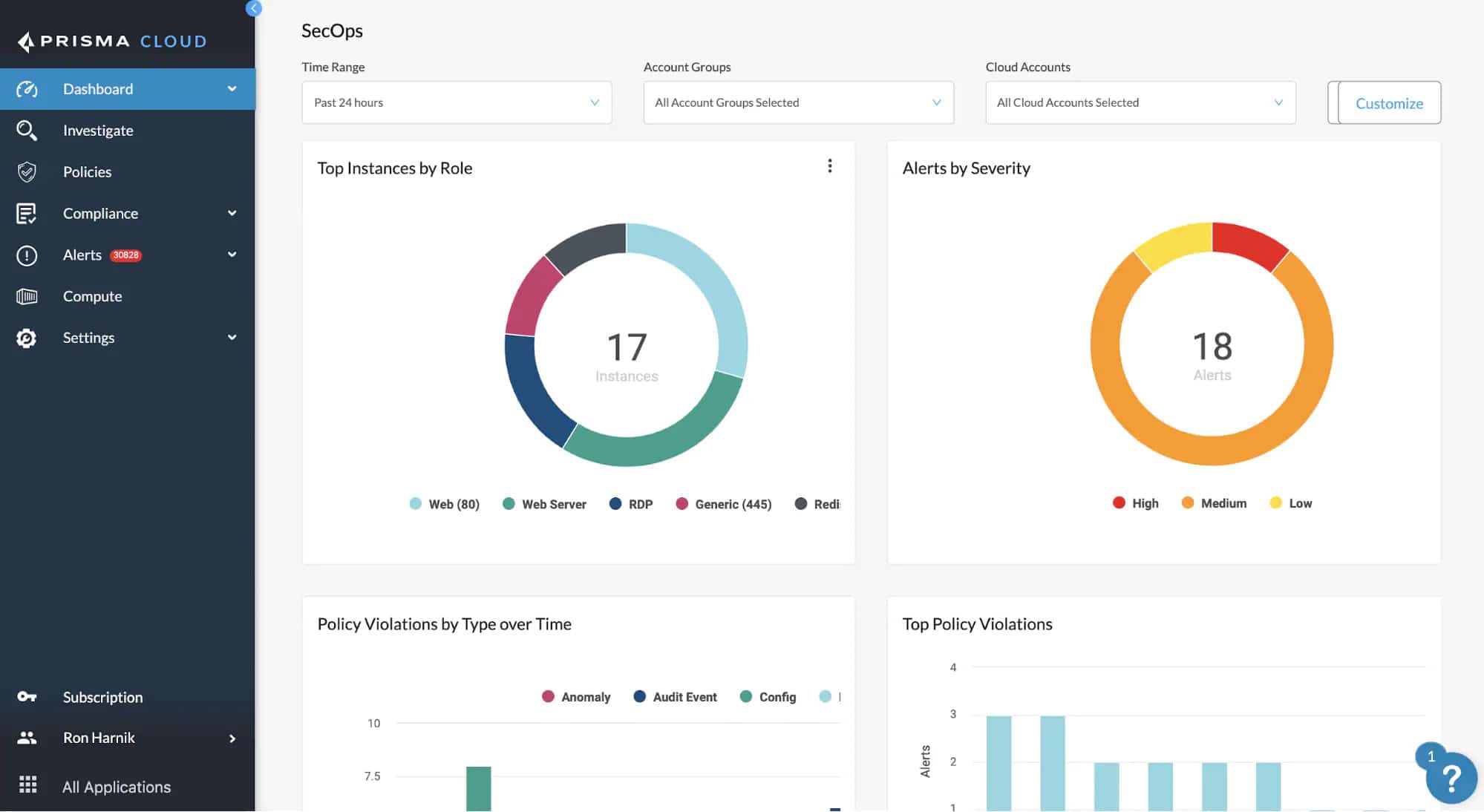
9. Prisma Cloud
Prisma Cloud is a best-in-class cloud-native security platform that offers unmatched visibility and protection across different platforms like Azure and Google Cloud. It also provides protection against unwanted threats using its advanced feature. Container image sandboxing is a new feature added to the leading CSPM tool that helps discover threats by inspecting all the files, processes, and pre-deployments of network activity.
Key Features
- Supported by Application Programming Interface (API)
- Prisma cloud provides regular backups
- Integrates with third-party systems
- Automates risk prioritization
- Provides full visibility
- Protects cloud-native development
- Network data exfiltration detection
- Enforcement of governance policies
- Scans malware on public cloud storage
- Microsegmentation
- Threat response
- Behavioral monitoring
- Ensures security to infrastructure, applications, hybrid, and multi-cloud environments
- Container security
- Threat detection
- API security
- Supports integration with continuous integration and continuous delivery (CI/CD) workflow
- Allows scanning of Infrastructure-as-Code (IaC) templates and container images
- Provides full-stack runtime protection
- Protects cloud workload, network, and security posture
Why do we recommend it?
Prisma Cloud stands out for its comprehensive, cloud-native security capabilities. Its unique feature of Container image sandboxing allows for deep inspection of files, processes, and network activity, significantly aiding in threat discovery and prevention.
Using Prisma cloud, developers can also discover and eliminate cloud blind spots. Further, with the help of Prisma cloud, the burden of alert fatigue is also reduced.
Prisma Cloud is a one-stop solution for all your cloud security needs that offers full control over public cloud environments, hosts, containers, and other platforms with its unified agent framework. It supports API security, and container security, and offers full-stack runtime protection, and full network visibility.
If you are looking for a CSPM tool that maintains compliance on multi and hybrid-cloud environments, go for Prisma Cloud.
Who is it recommended for?
Prisma Cloud is ideal for organizations operating in multi-cloud and hybrid-cloud environments who seek a unified approach to cloud security. Developers, cloud architects, and security teams that are focused on reducing alert fatigue and removing cloud blind spots will particularly benefit from its full-stack runtime protection and API security features.
Pros:
- Get full protection against unwanted threats
- Using Container image sandboxing, you can inspect all files/processes and quickly discover threats
- Helps remove cloud blind spits
- Helps reduce alert fatigue
- The tool offers full-stack runtime protection and visibility
Cons:
- Does not support the on-premises version
- Inadequate Documentation is available for manual search
Final Thoughts
CSPM are powerful tools that provide security to your cloud data and help identify misconfiguration issues and remediate risks across various cloud infrastructure. As more and more people are moving to cloud platforms, the need for powerful security tools has become a necessity.
This is where CSPM tools come into practice. These tools help detect compliance risks, and carry risk visualization and assessment capabilities. Further, they support alert systems to update cloud customers about threats and other security risks.
Using these tools, administrators can perform instance scanning for misconfigurations, maintain consistent enforcement across all cloud environments, monitor storage buckets, and conduct risk assessments.
We have also discussed various factors one must consider before investing their time and money into any of the above-listed CSPM tools.
In this blog, we have also shared some of the popular and top-notch CSPM tools including Prisma Cloud, Datadog, CrowdStrike Falcon, CloudGuard Posture Management (Dome9), Trend Micro Hybrid Cloud Security Solution, Threat Stack, and other tools that can be highly beneficial for your cloud security.
CSPM tools offer full visibility and protection to your cloud. Choose from a wide range of security tools and compare them using their features before making a final call.