Almost no single day goes without hearing or reading a piece of news about cyberattacks. Still, the ubiquity of attacks and the ability of hackers to pull it off so effortlessly (at least that’s how it looks because of the frequency) leads back to the question – what are we doing wrong?
Many things such as lower than optimal budgets, lack of awareness among employees about possible cybersecurity threats, limited measures in place to tackle attacks, lack of proactive monitoring, and more.
In this article, we will focus on the ways and means by which hackers can attack an organization and what you can do to bring down the different entry points in your network for hackers to enter and attack. Let’s start with an understanding of what an attack surface is and its importance, and then, move on to how you can bring it down.
What is an Attack Surface?
Attack surface is the combination of different entry points that hackers can potentially use to attack your organization’s network. It includes all the vulnerabilities and the devices or endpoints that can potentially provide an entry point for hackers.
Needless to say, the smaller the attack surface is, the lesser your chance to get attacked. This is why organizations strive to lower the area of their attack surface.
Now, on a practical note, attack surfaces are complex and widespread. In today’s world where work-from-home culture is highly prevalent, every device that connects to the organization’s network is a potential vulnerability. In this sense, the entire world is an attack surface for remote-model organizations.
Types of Attack Surfaces
Broadly speaking, an attack surface is categorized into physical and digital surfaces.
- Physical Attack Surfaces Physical attack surfaces encompass the physical space of an organization and include all the servers, data centers, devices, sensors, and other endpoints. It also includes security door access, paper documents containing sensitive information, physical devices, and basically, anything that a hacker can physically come and steal.
- Digital Attack Surfaces Digital attack surfaces are your applications, ports, remote devices, and other endpoints that can be virtually used by a hacker to enter your organization’s network. Often, the digital attack surfaces include vulnerabilities such as poor password practices, lack of employee training on best security practices, unpatched software, lack of role-based access to sensitive information, liberal configuration settings, and more.
Both the physical and digital attack surfaces must be kept to a minimum to stave off attacks.
How to Identify the Attack Surface Area?
The first step towards mitigating the possibility of an attack is to determine the size of your attack surface, so you know what measures should be put in place. This process of determining the size of your attack surface and all that it encompasses is called the attack surface analysis.
There are three broad steps for understanding your attack surface and they are:
- Visualization The first step is to create a map of all your devices, endpoints, physical spaces, and everything else that is a part of your organization’s network. This must include both digital and physical attack surfaces. You can imagine this step to be more of an inventory collection or gathering exercise.
- Looking out for Indicators The second step is to understand the possible indicators or vulnerabilities in the map that you visualized earlier. In this step, it’s a good idea to not just list down the different possible points of attack, but also jot down the strategies that could be used by hackers to enter the network through a particular endpoint. In this step, you can also include the necessary controls that are currently missing.
- As you can see, this step involves a detailed analysis of the strengths and weaknesses of your security system and the endpoints.
- Identifying Attacks This step is more of a retrospective analysis where you make a list of all the possible attacks that have happened and the strategy that hackers used each time to enter your network.
Armed with all this information, you are now set for a detailed attack surface analysis of what you should do and the strategies that you can leverage.
Attack Surface Analysis
Attack surface analysis is the process of identifying the endpoints that can allow a possible attack. It is a detailed analysis of the above-mentioned steps, so you know the number of exploitable vulnerabilities within your organization and what you can do to mitigate them. At the end of this analysis, you must be able to identify the areas that must be tested or reviewed for security vulnerabilities.
An attack surface analysis entails the following broad measures.
- Understand the vulnerabilities
- Inform the leadership/management about these vulnerabilities and their impact on the organization as a whole
- Find ways and means to mitigate the identified vulnerabilities
- Staying on top of how and when the attack surface area changes
Now that you have an idea of what an attack surface analysis is, let’s talk about the different strategies that you can use to achieve the above-mentioned aspects.
Attack Surface Analysis Strategies
Here’s a look at some strategies that can come in handy for your attack surface analysis.
Vulnerability Assessment
As the name suggests, this strategy is all about identifying and defining what a vulnerability is, identifying it, assessing the vulnerability for its impact, classifying the impact, and prioritizing them to beef up your network’s security. Many times, it can also include appropriate remediation recommendations to eliminate these vulnerabilities.
Some threats that can be prevented with vulnerability assessments include SQL injection, poor authentication mechanisms, faulty password policies that lead to the creation of simple and easily guessable passwords, and more.
Vulnerability assessments can be classified into many types, with the prominent ones being,
- Vulnerable Host Assessment This assessment includes identifying vulnerable devices and servers and includes patch management, outdated software, open ports, and more.
- Wireless and Network Assessment In this assessment, you look into the wireless connections and network vulnerabilities, especially the endpoints through which they can be accessed.
- Database Assessment This assessment includes assessing the security and authorization practices of databases, test and development environments, and more.
- Application Assessments In this assessment, you look into the codebase of applications and the possibility of security vulnerabilities.
In all, vulnerability assessments can help you identify threats and vulnerabilities.
Penetration Testing
Penetration testing or pen testing is the process of hiring ethical hackers to simulate an attack against your devices and network. The idea here is to get into the minds of hackers to understand how they are likely to attack your system. Accordingly, you can put the required security measures to prevent such attacks.
This proactive testing approach can also bring up the vulnerable practices and points from a security perspective, so they can be remediated at the earliest.
Red Team and Blue Team
Another popular strategy is to use two teams called the Red Team and the Blue Team. Typically, the Red team includes ethical hackers who try to hack into your system while the Blue team is your security personnel who try to prevent the attack and mitigate its impact.
The idea here is to prepare your security team to quickly prevent and handle any cyberattacks that can come up.
Thus, these are some examples of attack surface analysis that you can undertake for your organization.
At the outset, all of these analyses and practices can sound overwhelming. The good news is many attack surface analysis tools can ease this process for you.
Attack Surface Analysis Tools
Here’s a brief look at some of the most popular tools that can help with your attack surface analysis.
Our methodology for selecting the best attack surface analysis tool:
We’ve broken down our analysis for you based on these key criteria:
- Evaluates tool’s vulnerability detection capabilities.
- Assesses the scope of continuous monitoring offered.
- Analyzes the depth and utility of reporting features.
- Considers the ease of integration with existing systems.
- Reviews the availability of proactive remediation strategies.
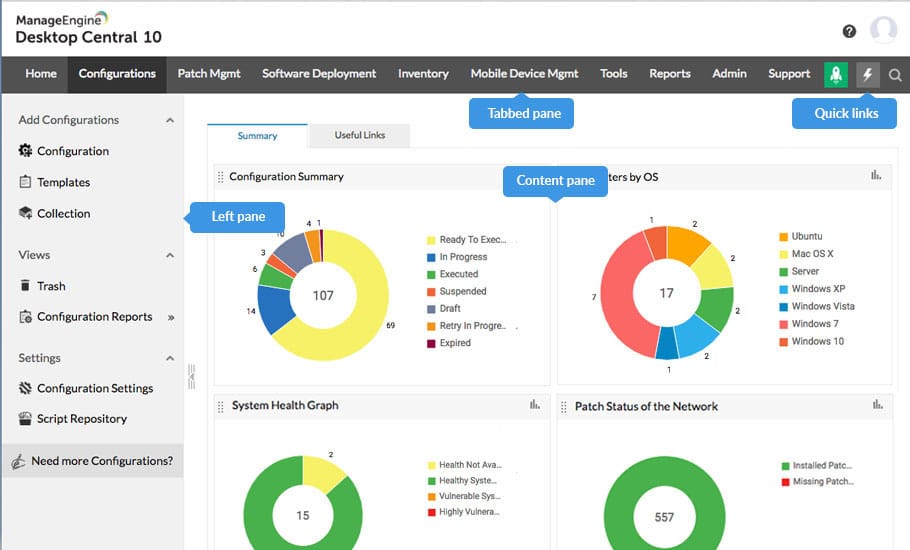
1. ManageEngine Endpoint Central – FREE TRIAL
Until recently, ManageEngine Endpoint Central was called Desktop Central and the system’s screens are still headed by the old name. This unified endpoint management package includes a full security service for endpoints. This includes a Vulnerability Management unit that provides attack surface scanning and system hardening features. The bundle also provides a next-generation anti-virus that scans for malware and a user behavior analytics service that spots insider threats and account takeovers.
Key Features:
- Comprehensive Endpoint Management: Offers a unified platform for device management and security.
- Vulnerability Management: Provides tools for attack surface scanning and system hardening.
- Next-Generation Antivirus: Includes advanced malware scanning capabilities.
- User Behavior Analytics: Detects insider threats and account takeovers.
Why do we recommend it?
Businesses that supply users with mobile devices or allow them to access company resources through their own devices need to manage endpoints and also enforce security. There are many ways that malware and hackers can get onto your system to create havoc or steal data and ManageEngine Endpoint Central includes a range of security tools to combat threats.
Who is it recommended for?
This is a very large package of device management and security systems. It includes a full vulnerability manager and patch manager to prevent attacks and it also includes ongoing security scanning to block attacks in progress. Second-line defenses for data prevent insider threats and account takeovers from resulting in data theft. The system also includes a next-generation AV to block malware.
ManageEngine offers Endpoint Central as a SaaS platform but you can also choose to download the software and run it yourself on Windows Server. Both deployment options offer five plan levels. The Security Edition includes all of the system protection services available in the package – those features are available to the buyers of the other plans as add-ons. There is one exception to that configuration – the Free Edition has all of the modules in Endpoint Central fully activated. The Free Edition has the full vulnerability management and data protection systems but it is limited to protecting 25 endpoints. The Security Edition’s price starts at $1,695. Start by downloading the 30-day free trial.
Pros:
- Holistic Security Tools: Bundles a range of defenses against malware, hackers, and internal threats.
- Full Vulnerability and Patch Management: Equips businesses to preemptively block attacks and maintain system integrity.
- Next-Gen Malware Protection: Features a sophisticated antivirus to counteract various malware forms.
- Insider Threat Mitigation: Identifies and neutralizes potential internal security breaches.
Cons:
- Complexity for Small Businesses: The extensive feature set may overwhelm smaller organizations.
- Pricing Structure: The full suite of security features necessitates purchasing the Security Edition or add-ons, which can be costly.
EDITOR'S CHOICE
ManageEngine Endpoint Central is our top pick for an attack surface management package because this system is available in both online and on-premises versions and it offers a great deal of plan flexibility. There are many security modules available in Endpoint Central but only the Security Edition and the Free Edition include all of them. Buyers of the other plans can pick and choose which security modules to add on. Those add-ons are charged for and they include the Vulnerability Detection unit, which provides attack surface scanning. Small businesses will be pleased to learn that the Free edition includes all of the modules, including the Vulnerability Detection system and covers up to 25 endpoints.
Download: Download a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/desktop-central/free-trial.html
OS: <span>Windows Server and cloud</span>
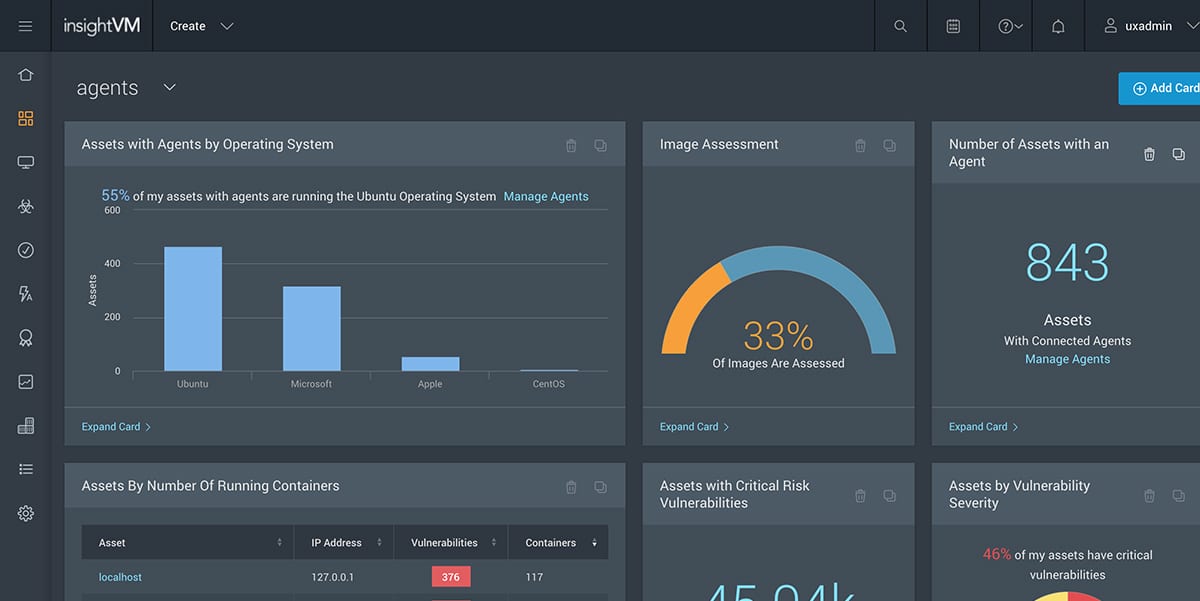
2. Rapid7 InsightVM
Rapid7 is a comprehensive tool that helps to implement many strategies such as exposure analytics, data scans, global attacker behavior, and more. It even comes with real-time reporting to help you stay on top of your vulnerabilities. This tool also scales well as your organization grows.
Key Features:
- Exposure analytics
- Real-time reporting
- Scalable solution
Why do we recommend it?
Rapid7 InsightVM stands out for its comprehensive approach to vulnerability management, offering features like exposure analytics, real-time reporting, and scalability. The tool’s affordable pricing at $1.84/month per asset, along with a free trial option, offers good value for its capabilities.
Who is it recommended for?
InsightVM is suitable for organizations of all sizes that require a multifaceted approach to vulnerability management. Its scalability and real-time reporting make it ideal for growing businesses, while its affordability per asset ensures it’s also a viable option for smaller enterprises or projects with a tight budget.
Pros:
- Comprehensive vulnerability management
- Scalable for growing organizations
- Free trial option available
Cons:
- Might be complex for small-scale users
This tool is also highly affordable at $1.84/month per asset. Click here to get an accurate quote based on your assets. You can also have a free trial of this tool.
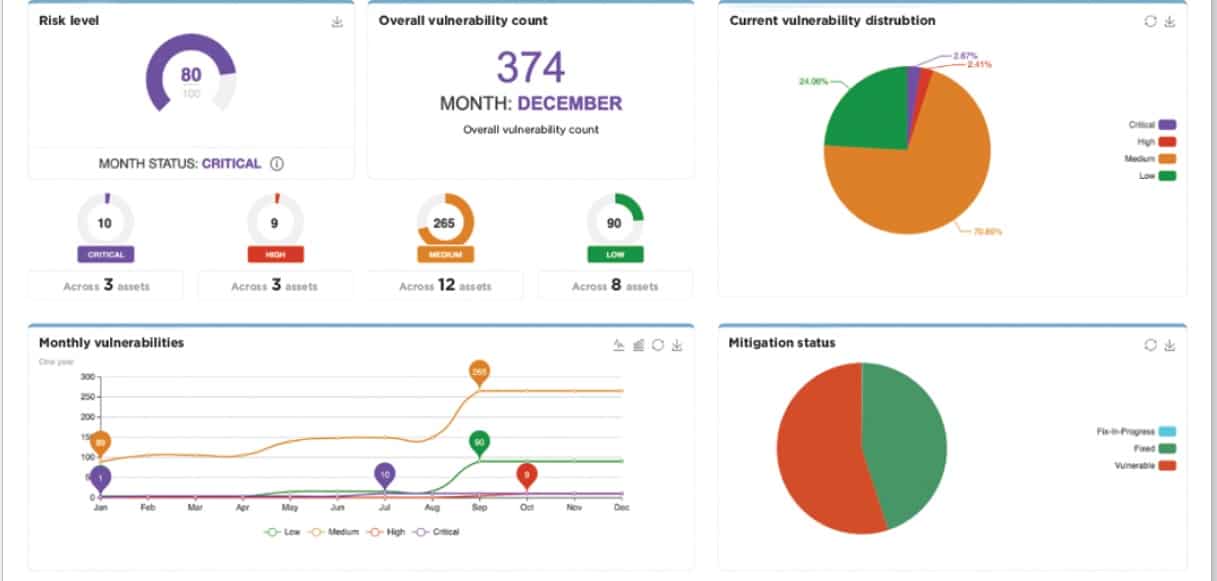
3. CoalFire Attack Surface Management
Coalfire offers a continuous attack surface management solution that examines your endpoints at all times for vulnerabilities. It also generates advanced reports that detail the vulnerabilities and their likely impact on your organization. In some cases, it also suggests appropriate remediation strategies.
Key Features:
- Continuous endpoint monitoring
- Advanced reporting capabilities
- Remediation strategy suggestions
Why do we recommend it?
CoalFire Attack Surface Management provides a continuous, proactive approach to identifying vulnerabilities on your endpoints. It not only detects vulnerabilities but also generates detailed reports and suggests remediation strategies, enabling organizations to stay one step ahead of potential cyber threats.
Who is it recommended for?
This solution is ideal for organizations that are looking for an all-inclusive approach to attack surface management. Its capabilities in vulnerability detection, detailed reporting, and remediation suggestions make it suitable for businesses that require a proactive and thorough cyber defense strategy.
Pros:
- Proactive vulnerability detection
- Suggests remediation strategies
- Comprehensive cyber defense approach
Cons:
- May require technical expertise for maximum benefit
All this information helps you to proactively stave off cyberattacks and even stay ahead of hackers in the event of an attack. You can even track the remediation efforts and prioritize them as needed. In all, a comprehensive solution to attack surface analysis and management.
Contact the customer team for a custom quote.
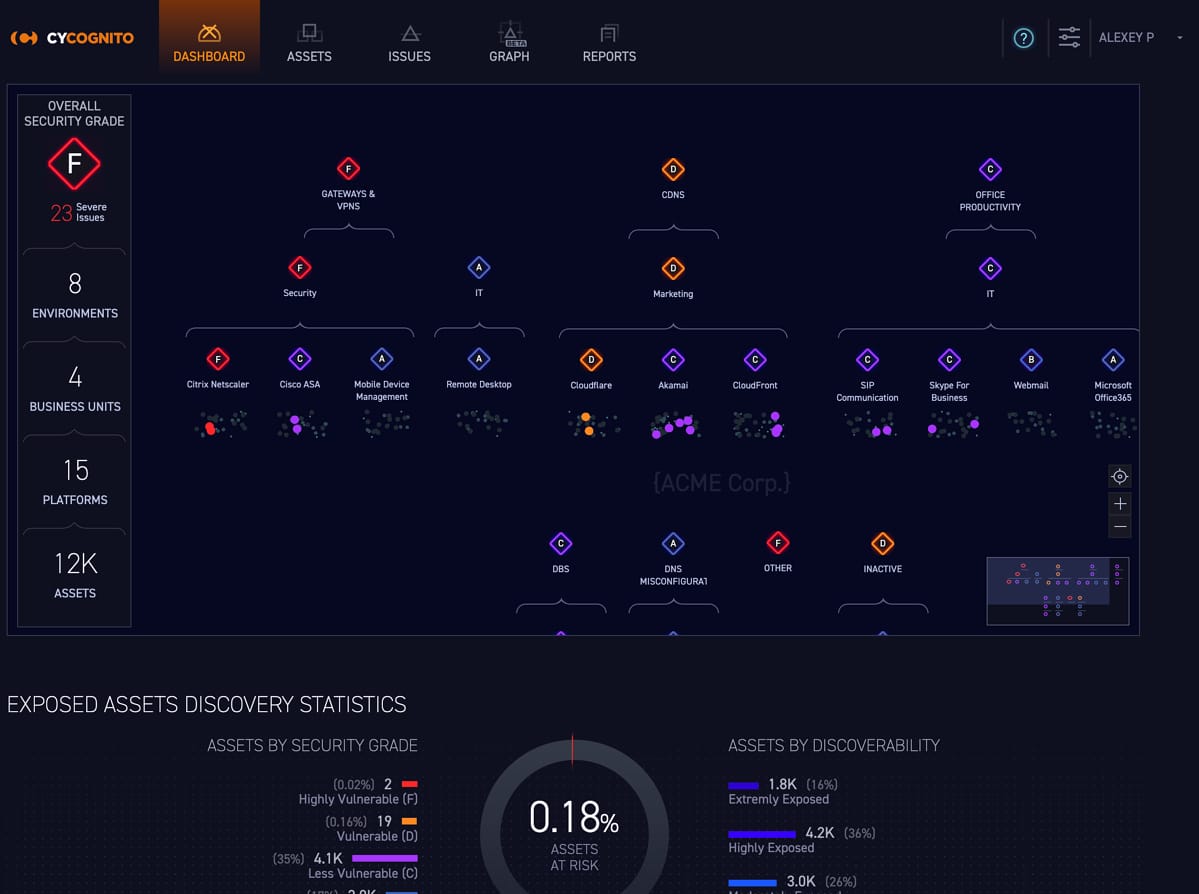
4. CyCognito Attack Surface Management
CyCognito is a cloud-based attack surface management tool that provides continuous visibility into your attack surface area and monitors the same for existing and new vulnerabilities. Using its real-time reports, you can discover risks, prioritize them, and even remediate them at the earliest to protect your organization from possible attacks.
Key Features:
- Continuous, real-time monitoring
- Visibility into attack surface
- Efficient risk prioritization
Why do we recommend it?
CyCognito Attack Surface Management offers continuous, real-time visibility into your attack surface, helping to identify both existing and emerging vulnerabilities. Its capabilities in risk prioritization and prompt remediation make it a standout tool for maintaining organizational security.
Who is it recommended for?
This cloud-based tool is particularly beneficial for organizations that require continuous monitoring and real-time reporting to manage their attack surface. It’s a strong fit for companies that want to proactively discover, prioritize, and address vulnerabilities to safeguard their operational integrity.
Pros:
- Real-time visibility and monitoring
- Identifies new and existing vulnerabilities
- Effective for operational security maintenance
Cons:
- Could be complex for smaller organizations without dedicated IT teams
Contact the customer support team for a quote. Click here to watch a demo video of how this tool can protect your organization.
Thus, these are some popular choices for your attack surface analysis and management.
Conclusion
To conclude, an attack surface is a physical and digital area that a hacker can leverage to attack your organization. This can include endpoints such as devices, servers, applications, networks, and more. In today’s work-from-home culture, this attack surface area is as wide as your employees’ work location, and this is why it is more important now than ever before to stay on top of attacks.
The above-mentioned attack surface analysis strategies and tools can help you in this regard.