Create a configuration file like this:
[ req ] default_md = sha1 default_bits = 2048 distinguished_name = req_distinguished_name encrypt_key = no string_mask = nombstr x509_extensions = req_ext UID = netadmintools UID_default="https://netadmintools.com/foaf.rdf#me" [ req_distinguished_name ] commonName = netadmintools.com commonName_default = WebID for NetAdminTools Webmaster [ req_ext ] subjectKeyIdentifier = hash subjectAltName = critical,@subject_alt basicConstraints = CA:false extendedKeyUsage = clientAuth nsCertType = client [ subject_alt ] URI.1="https://netadmintools.com/foaf.rdf#me" |
Run this command to create your certificate:
openssl req -new -batch -days 3650 -config config.txt \ -out webid.pem -extensions req_ext -x509 -keyout webid.pem |
You should see something like this:
Generating a 2048 bit RSA private key .............................................+++ ..........+++ writing new private key to 'webid.pem' ----- |
Verify the certificate:
openssl x509 -in webid.pem -noout -text |
The output should look like this:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
.
.
.
Subject: CN=WebID for NetAdminTools Webmaster
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
.
.
.
Exponent: 65537 (0x10001)
.
.
.
X509v3 Extended Key Usage:
TLS Web Client Authentication
Netscape Cert Type:
SSL Client
Signature Algorithm: sha1WithRSAEncryption
|
Run this command:
openssl rsa -in webid.pem -modulus -noout |
You will need this for your rdf file:
Modulus=EED53866F554F0B2C9283F1E4B7A004EA0EE378DDE6CC0363DF4D7249B3D4892E 7C22D2B0193F4376D321881071A42B40BCE35067B70622B36E8FEE8B9255127756A6AE645 4A06A03ADCF6DB44BCC7A1575ABDF294EC18D74B1EE8035901D6416B034E29C31805D0CE A87EB365D82C91869EAB2B161C27DFDC6D51E232A5C55B40A04D0183CACA3A72FFC8AEEC D13DF5FE608C1458B5648512AAA30A1BDF80C7240B013D6FBAB6A3BA1699CA6CF3641F0E1 B05F1F013A673D35CD9D6DF03460C0FC5823D28DCD48D1FE4A44B8D9429731F9ADDCD06 8337BE48D8ED3D77749CABD47A1E64CC67FE935511CD41325C3984F8CC1A6AB142A601FBF 8CA8C6D5EE157 |
This is what the foaf.rdf file for Netadmintools.com looks like:
<?xml version="1.0"?>
<rdf:RDF
xmlns:rdf="http://www.w3.org/1999/02/22-rdf-syntax-ns#"
xmlns:cert="http://www.w3.org/ns/auth/cert#"
xmlns:foaf="http://xmlns.com/foaf/0.1/">
<foaf:Person rdf:about="https://netadmintools.com/foaf.rdf#me">
<foaf:name></foaf:name>
<foaf:givenname>NetAdminTools</foaf:givenname>
<foaf:family_name>Webmaster</foaf:family_name>
<foaf:nick>netadmintools</foaf:nick>
<foaf:homepage rdf:resource="https://netadmintools.com"/>
<foaf:depiction rdf:resource="http://stage.netadmintools.com/images/translogo.gif"/>
<cert:key>
<cert:RSAPublicKey>
<cert:modulus rdf:datatype="http://www.w3.org/2001/XMLSchema#hexBinary">EED53866F
554F0B2C9283F1E4B7A004EA0EE378DDE6CC0363DF
4D7249B3D4892E7C22D2B0193F4376D321881071A42B40BCE35067B70622B36E8FEE8B925
5127756A6AE6454A06A03ADCF6DB44BCC7A1575ABDF294EC18D74B1EE8035901D6416B03
4E29C31805D0CEA87EB365D82C91869EAB2B161C27DFDC6D51E232A5C55B40A04D0183CA
CA3A72FFC8AEECD13DF5FE608C1458B5648512AAA30A1BDF80C7240B013D6FBAB6A3BA169
9CA6CF3641F0E1B05F1F013A673D35CD9D6DF03460C0FC5823D28DCD48D1FE4A44B8D942
9731F9ADDCD068337BE48D8ED3D77749CABD47A1E64CC67FE935511CD41325C3984F8CC1
A6AB142A601FBF8CA8C6D5EE157</cert:modulus>
<cert:exponent rdf:datatype="http://www.w3.org/2001/XMLSchema#integer">65537</cert:exponent>
</cert:RSAPublicKey>
</cert:key>
</foaf:Person>
</rdf:RDF>
|
Create a certificate to import into your browser:
openssl pkcs12 -export -clcerts -name "WebID for NetAdminTools" -in webid.pem \ -inkey webid.pem -out webid.p12 |
You’ll be asked for a password that will give you some protection while the cert.
Enter Export Password: Verifying - Enter Export Password: |
Import the cert into your browser. On Chrome it is in settings/advanced settings/manage certificates/your certificates/import. On Firefox it is in preferences/advanced/encryption/view certificates/import. On the iPhone (I’m using iOS 6.0.1), just email yourself the cert and open it. You can then import it:
To test out the profile, go to a site that supports WebID. One good site is MyProfile. You will get
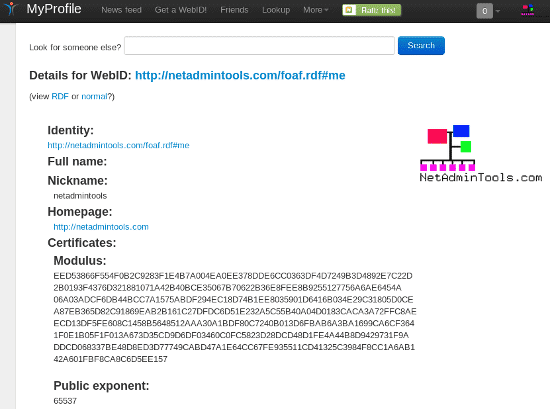
Here is what the Netadmintools.com profile looks like: