Nothing is worse than having an intrusion in your network perimeter and knowing that someone has had access to your filesystems and personal information. One of the greatest fears of many network admin’s and engineers is their network and computer/servers being compromised by a malicious attacker.
There is No Better way of assessing your infrastructures security and possible vulnerabilities than running an array of network penetration testing tools against your network and patching up any holes or mis-configurations as you find them.
Here is our list of the best network security software and frameworks for pen-testing and vulnerability assessment:
- ManageEngine Vulnerability Manager Plus – FREE TRIAL A comprehensive vulnerability scanner and remediation tool rich with automated features. Get a fully functional 30-day free trial.
- Nikto Simple lightweight CLI-based vulnerability scanner.
- OpenVAS A popular framework for vulnerability identification and detection.
- Acunetix A popular GUI alternative to OpenVAS.
- NMap A highly flexible lightweight CLI tool used for network vulnerability detection.
- Burp Suite A popular penetration testing platform for security researchers.
We recommend all engineers go through the necessary steps to patching up systems, firewalls and routers in order to keep intruders out. So we’ve gone through a list of the top network security tools and frameworks to use in your process of hardening your infrastructure. We also recommend actively monitoring your network to keep tabs on systems that could possibly be using more bandwidth than necessary – these are all signals of an intrusion.
The Top Network Security Tools for Assessing Vulnerabilities & Exploits
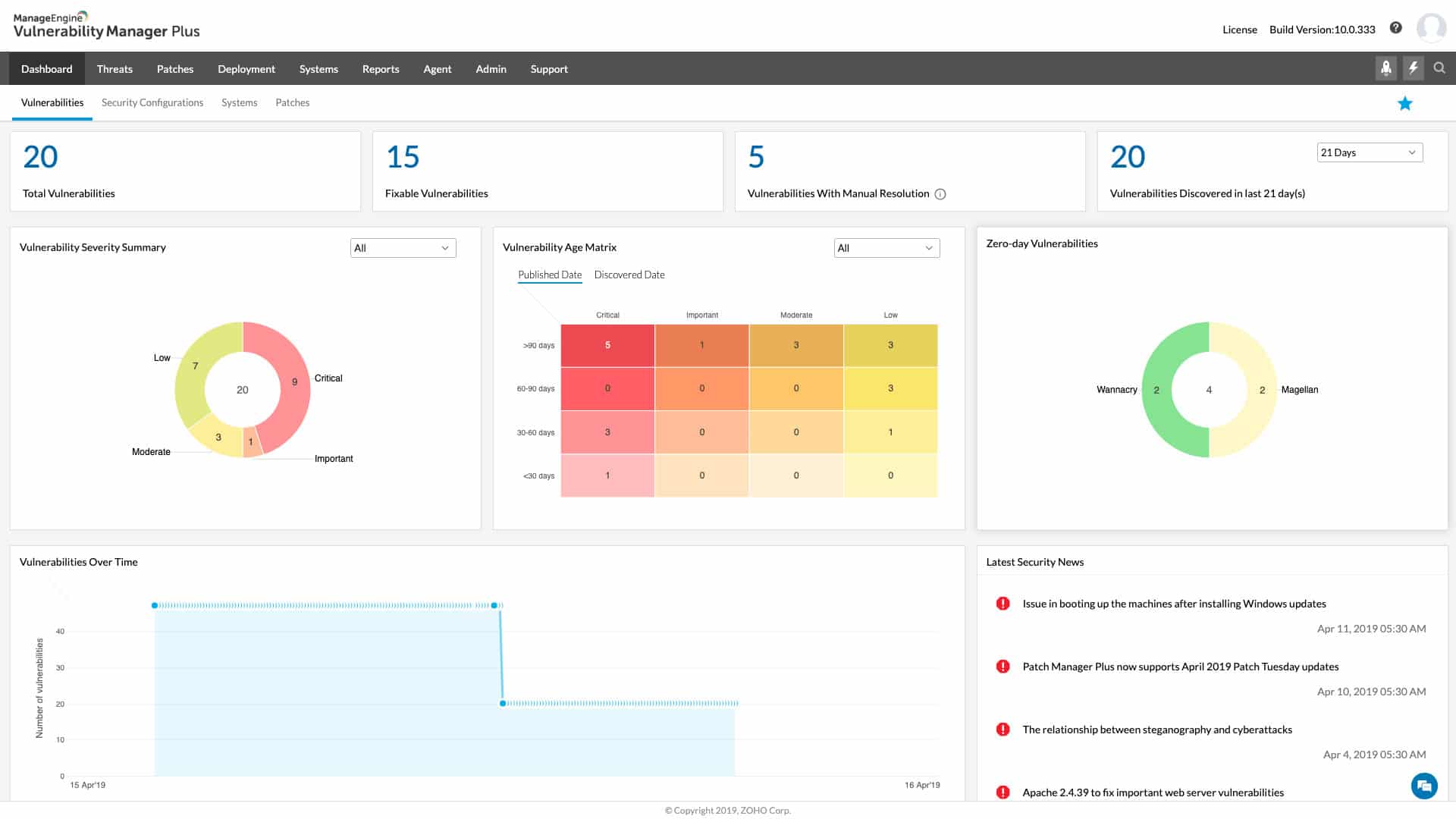
1. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus is a remediation platform that helps companies locate and address vulnerabilities in their devices and network. The program utilizes continuous scanning to identify potential vulnerabilities, such as outdated patches or insecure configurations and then generates comprehensive reports on the findings.
Key Features
- Automated remediation
- Detailed reporting
- Intuitive UI
Why do we recommend it?
We installed the free trial of ManageEngine Vulnerability Manager Plus and were impressed by its automated remediation and continuous scanning features. The platform not only identifies vulnerabilities but also offers comprehensive remediation recommendations, making it a robust tool for enhancing network security.
Vulnerability Manager Plus offers asset management, patch management, and compliance reporting features in addition to vulnerability detection to help enterprises maintain the security of their IT infrastructure. To help businesses fix the vulnerabilities that have been detected, the software also provides remediation recommendations. These recommendations include comprehensive instructions and links to pertinent resources.
Who is it recommended for?
ManageEngine Vulnerability Manager Plus is ideal for enterprises that require an all-in-one vulnerability management solution. If your organization needs to regularly scan for vulnerabilities, manage patches, and comply with various security standards, this tool will serve you well. It’s also suitable for businesses that have a diverse range of operating systems, given its flexibility.
Pros:
- Continuous scanning and patching throughout the lifecycle of any device
- Robust reporting can help show improvements after remediation
- Flexible – can a variety of operating systems
- Backend threat intelligence is continuously updated with the latest threats and vulnerabilities
- Provides flexible pricing and deployment options
Cons:
- VMP is a feature-rich platform that can take time to fully explore
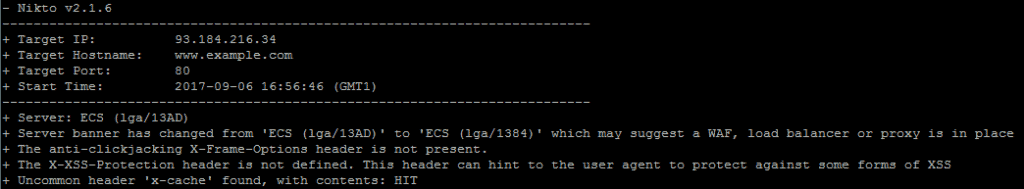
2. Nikto
Nikto is old, however, it can still detect far more vulnerabilities than other web scanners out there. Because of this Nikto has a good reputation find pinpointing vulnerabilities in web apps and old web servers.
Why do we recommend it?
After running Nikto in a sandbox environment, we found it exceptionally proficient in detecting a broad spectrum of vulnerabilities, including outdated CGI scripts and web server issues. Its speed and comprehensive ‘Tuning’ feature stood out, allowing us to focus on specific vulnerabilities like SQL injection effectively.
Nikto is also extremely fast and capable of detecting up to 6400 potentially dangerous files/CGI scripts and can check for 1200 web server-related problems across a span of over 270 web server builds.
Who is it recommended for?
Nikto is best suited for security professionals and IT teams that deal with older web servers and applications. It’s a go-to tool if you need a fast and thorough vulnerability scanner capable of identifying a wide range of issues. The tool is also beneficial for those looking to perform deep dives into specific types of vulnerabilities, thanks to its customizable ‘Tuning’ options.
This scanner offers the ability to do much more than just identify web server vulnerabilities, it can detect host information, brute force authentication forms, guess subdomains, report unusual header information, and schedule and pause scans. Using Nikto’s ‘Tuning’ feature, you can also specifically target certain types of vulnerabilities like SQL injection, file uploads, remote file retrieval, etc.
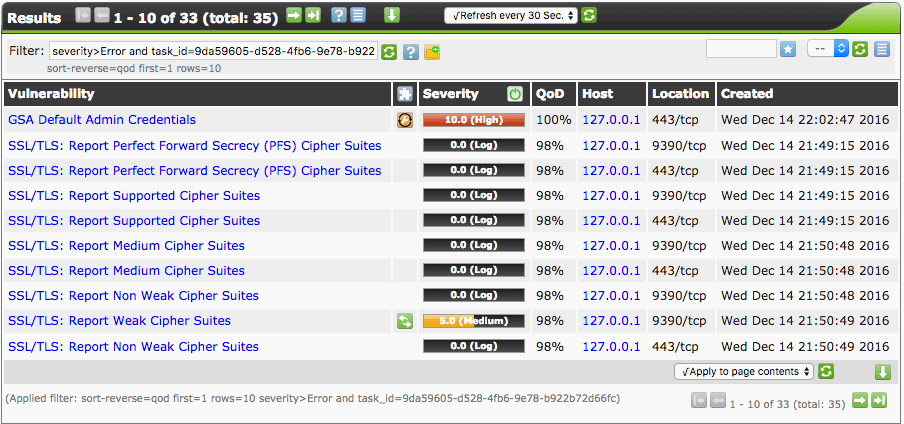
3. OpenVAS
OpenVAS is a framework that has been built to incorporate lots of individual security tools and services to provide mass vulnerability scanning. One reason it is so popular is because it is community-built and completely free. You can run OpenVAS via CLI or with a web GUI as shown above, it’s fast and also allows you to export detailed ‘Executive’ summary style reports.
Why do we recommend it?
After setting up OpenVAS and conducting tests on multiple targets, we were impressed by its comprehensive framework that integrates a multitude of individual security tools. Despite not being the fastest scanner, its daily updated feed of Network Vulnerability Tests made it remarkably thorough in identifying vulnerabilities in large networks.
OpenVAS can be broken down into four specific functional components. OpenVAS Scanner provides the ability to scan target hosts concurrently and via SSL. OpenVAS Manager essentially provides the ability to store results via SQL, manage the scanner and schedule scans. It also offers the ability to report results and essentially is the main OpenVAS application. Greenbone Security Assistant (GSA) provide a HTTP/Web interface for OpenVAS and OpenVAS CLI provides the command line interface.
Who is it recommended for?
OpenVAS is ideal for enterprises and organizations with large networks that require a deep and comprehensive security analysis. It is especially useful for security analysts, network administrators, and compliance officers who need detailed reports and the flexibility to schedule scans. Given its open-source nature, it’s also a great choice for community-driven projects looking for a robust, cost-effective vulnerability scanning solution.
OpenVAS receives a daily update feed of Network Vulnerability Tests (NVTs) and as of June 2016 had over 47,000 active vulnerability tests. OpenVAS has been designed to support scanning large subnets and although it’s not the fastest scanner, it incorporates so many tools and vulnerability identification kits from other GPL projects it can provide excellent insight into the status of security in large networks.
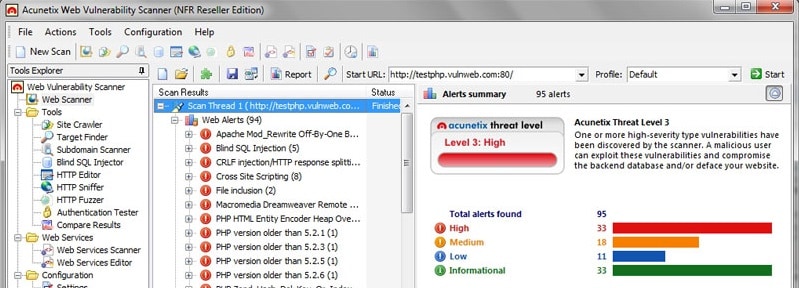
4. Acunetix
Acunetix is similar to OpenVAS, however can only be used via a GUI interface, and it’s also currently a product you have to pay for. Acunetix boasts a huge amount of checks for web applications and it is known more for web app penetration testing. Acunetix can detect 3000 web application vulnerabilities and supports multi-thread scanning for fast results.
Why do we recommend it?
We downloaded the 14-day free trial of Acunetix and ran it through a series of web application tests. The software’s multi-thread scanning and AcuSensor technology caught our attention, delivering fast and precise results while identifying 3000 different web application vulnerabilities with fewer false positives.
Acunetix can intelligently audit code for common vulnerabilities such as SQL injection, and even conduct automatic brute force attacks to check for weak passwords. AcuSensor technology allows you to identify more vulnerabilities with less false positives and produces an overall more accurate web assessment of the target. Acunetix is also one of the only scanners with full HTML5 support and mobile website scanning support.
Who is it recommended for?
Acunetix is highly recommended for web application developers, penetration testers, and security auditors. With its focus on web app penetration testing and features like HTML5 and mobile website scanning, it’s particularly beneficial for businesses that prioritize web and mobile app security. The software is also suitable for teams that appreciate a GUI interface and bundled manual testing tools.
You also get a bundle of built-in tools for performing manual checks, these include the HTTP Editor/Fuzzer and Sniffer, subdomain scanner, and site crawler which all help gather information on the target.
5. Nmap (Free & Open-Source)
Everyone knows NMAP! It is a port scanner, and one of the best due to its advanced scanning features. Aside from simply scanning you can perform more advanced recon and learn to hack like a pro with its unique features like; decoying, firewall evasion, scripting, and list imports and exports.
Why do we recommend it?
After using Nmap extensively in our sandbox environment, we were particularly impressed by its advanced scanning features like firewall evasion and scripting capabilities. Its NSE scripts add another layer of sophistication, allowing for detailed vulnerability discovery and even exploitation.
One of Nmap’s best features is its ability to use NSE scripts to actually discover, fuzz, and exploit hosts for vulnerabilities such as the 2014 shellshock flaw. The ability to integrate scripts into scans allows you to take advantage of a huge amount of preconfigured ‘auto enumerate’ scripts that can target specific ports and services like SNMP to gather more information.
Who is it recommended for?
Nmap is an ideal tool for network administrators, cybersecurity researchers, and ethical hackers who want to perform in-depth network analysis and vulnerability assessments. The tool’s versatility makes it suitable for both beginner and advanced users, and the availability of a GUI version through Zenmap offers a more user-friendly experience for those less comfortable with CLI.
Although this tool is primarily used in CLI format from bash or command prompt on Windows, Zenmap has developed a GUI version of the tool, allowing you to use most of Nmaps features from a GUI, and it contains some nice additional features such as smart search.
6. Burp Suite
Burp Suite is one of the most popular penetration testing tools for professionals. It allows advanced scanning and vulnerability identification for manual penetration testers. Burps proxy feature allows you to point your web browser at the built-in proxy server, which allows for direct tampering of the http data.
Why do we recommend it?
We tested Burp Suite in our sandbox environment and found its features like Decoder and Repeater to be extremely valuable for manual penetration testing. The built-in proxy server facilitated the direct tampering of HTTP data, and the tool’s capability to decode data back to plain text provided invaluable insights.
Burps built-in scanner lets you detect simple web application issues fast, like if you submit data via GET method, or have active SQL injection flaws in your code.
Burp also has a great feature called Decoder. Often applications transmit and receive data that is encoded as developers believe it to secure code, however it does not. Decoder can take the transmitted encoded data, and decode it back to plain text.
Who is it recommended for?
Burp Suite is a must-have tool for professional penetration testers, cybersecurity experts, and developers focused on web application security. Its advanced capabilities make it less suitable for casual users but invaluable for those who are serious about identifying and rectifying web application vulnerabilities.
Repeater is one of the best features of Burp suite. You can select a request from a target and send it to Repeater to further tamper and play-around with the request by changing the data that gets sent such as cookie information.
Conclusion
We hope you found this article useful and can use it to help better protect your internet-facing networks from cyber-attacks. As with all technologies, if you do not understand some concepts or how to use them properly and in a manner where you don’t bring your own network DOWN, you should hire a professional network security auditor or cyber security professional from an online job boards.
As of recently, there have been several Cyber Security jobs websites that are tailored specifically for Pen-testers and ethical hackers.
Cyber Security professionals are in high demand due to their extensive skill sets of pen-testing and vulnerability assessment using the programs above and many others to gather intelligence and properly document ways to patch them.
As more ransomware attacks and corporate espionage attacks consistently happen, the more these types of jobs become the center of focus for many corporations.